A network administrator has just added a front desk receptionist account to the Cisco ISE Guest Service sponsor group. Using the Cisco ISE Guest Sponsor Portal, which guest services can the receptionist provide?
A.
Keep track of guest user activities
B.
Configure authorization settings for guest users
C.
Create and manage guest user accounts
D.
Authenticate guest users to Cisco ISE
Create and manage guest user accounts
Which personas can a Cisco ISE node assume'?
A.
policy service, gatekeeping, and monitoring
B.
administration, policy service, and monitoring
C.
administration, policy service, gatekeeping
D.
administration, monitoring, and gatekeeping
administration, policy service, and monitoring
https://www.cisco.com/en/US/docs/security/ise/1.0/user_guide/ise10_dis_deploy.html
The persona or personas of a node determine the services provided by a node. An ISE node can assume any or all of the following personas: Administration, Policy Service, and Monitoring. The menu options that are available through the administrative user interface are dependent on the role and personas that an ISE node assumes. See Cisco ISE Nodes and Available Menu Options for more information.
A user reports that the RADIUS accounting packets are not being seen on the Cisco ISE server.
Which command is the user missing in the switch’s configuration?
A.
radius-server vsa send accounting
B.
aaa accounting network default start-stop group radius
C.
aaa accounting resource default start-stop group radius
D.
aaa accounting exec default start-stop group radios
radius-server vsa send accounting
Which two endpoint compliance statuses are possible? (Choose two.)
A.
unknown
B.
known
C.
invalid
D.
compliant
E.
valid
unknown
compliant
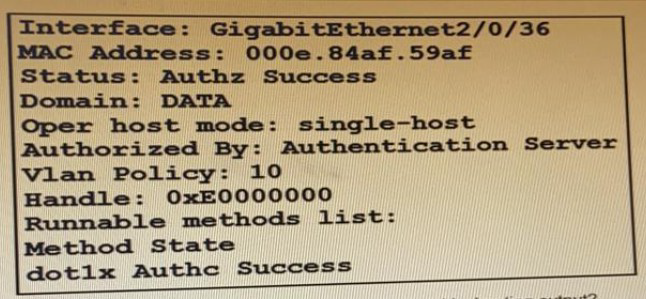
Refer to the exhibit:
A.
show authentication sessions mac 000e.84af.59af details
B.
show authentication registrations
C.
show authentication interface gigabitethemet2/0/36
D.
show authentication sessions method
show authentication sessions mac 000e.84af.59af details
Which two methods should a sponsor select to create bulk guest accounts from the sponsor portal? (Choose two )
A.
Random
B.
Monthly
C.
Daily
D.
Imported
E.
Known
Random
Imported
Which configuration is required in the Cisco ISE authentication policy to allow Central Web Authentication?
A.
MAB and if user not found, continue
B.
MAB and if authentication failed, continue
C.
Dot1x and if user not found, continue
D.
Dot1x and if authentication failed, continue
MAB and if user not found, continue
What must match between Cisco ISE and the network access device to successfully authenticate endpoints?
A.
SNMP version
B.
shared secret
C.
certificate
D.
profile
shared secret
Which two probes must be enabled for the ARP cache to function in the Cisco ISE profile service so that a user can reliably bind the IP address and MAC addresses of endpoints? (Choose two.)
A.
NetFlow
B.
NetFlow
C.
SNMP
D.
HTTP
E.
DHCP
F.
RADIUS
HTTP
DHCP
Cisco ISE implements an ARP cache in the profiling service, so that you can
reliably map the IP addresses and the MAC addresses of endpoints. For the ARP cache to
function, you must enable either the DHCP probe or the RADIUS probe. The DHCP and
RADIUS probes carry the IP addresses and the MAC addresses of endpoints in the
payload data. The dhcp-requested address attribute in the DHCP probe and the Framed-
IP-address attribute in the RADIUS probe carry the IP addresses of endpoints, along with
their MAC addresses, which can be mapped and stored in the ARP cache.
https://www.cisco.com/c/en/us/td/docs/security/ise/2-
1/admin_guide/b_ise_admin_guide_21/b_ise_admin_guide_20_chapter_010100.html
Which are two characteristics of TACACS+? (Choose two ) ,
A.
It uses TCP port 49.
B.
It combines authorization and authentication functions
C.
It separates authorization and authentication functions.
D.
It encrypts the password only.
E.
It uses UDP port 49.
It uses TCP port 49.
It separates authorization and authentication functions.
Which profiling probe collects the user-agent string?
A.
DHCP
B.
AD
C.
HTTP
D.
NMAP
HTTP
Which two responses from the RADIUS server to NAS are valid during the authentication process? (Choose two )
A.
access-response
B.
access-request
C.
access-reserved
D.
access-accept
E.
access-challenge
access-request
access-accept
| Page 5 out of 20 Pages |
| Previous |