Which two features are available when the primary admin node is down and the secondary admin node has not been promoted? ()
A.
hotspot
B.
new AD user 802 1X authentication
C.
posture
D.
BYOD
E.
guest AUP
new AD user 802 1X authentication
posture
If a user reports a device lost or stolen, which portal should be used to prevent the device from accessing the network while still providing information about why the device is blocked?
A.
Client Provisioning
B.
Guest
C.
BYOD
D.
Blacklist
Blacklist
https://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/Borderless_Networks/Unified_A ccess/BYOD_Design_Guide/Managing_Lost_or_Stolen_Device.html#90273
The Blacklist identity group is system generated and maintained by ISE to prevent access to lost or stolen devices. In this design guide, two authorization profiles are used to enforce the permissions for wireless and wired devices within the Blacklist:
✑ Blackhole WiFi Access ✑ Blackhole Wired Access
What must be configured on the Cisco ISE authentication policy for unknown MAC addresses/identities for successful authentication?
A.
pass
B.
reject
C.
drop
D.
continue
continue
How is policy services node redundancy achieved in a deployment?
A.
by enabling VIP
B.
by utilizing RADIUS server list on the NAD
C.
by creating a node group
D.
by deploying both primary and secondary node
by creating a node group
Which two events trigger a CoA for an endpoint when CoA is enabled globally for ReAuth? (Choose two.)
A.
endpoint marked as lost in My Devices Portal
B.
addition of endpoint to My Devices Portal
C.
endpoint profile transition from Apple-Device to Apple-iPhone
D.
endpoint profile transition from Unknown to Windows 10-Workstation
E.
updating of endpoint dACL.
endpoint profile transition from Apple-Device to Apple-iPhone
endpoint profile transition from Unknown to Windows 10-Workstation
What sends the redirect ACL that is configured in the authorization profile back to the Cisco WLC?
A.
Cisco-av-pair
B.
Class attribute
C.
Event
D.
State attribute
Cisco-av-pair
Drag the Cisco ISE node types from the left onto the appropriate purposes on the right.
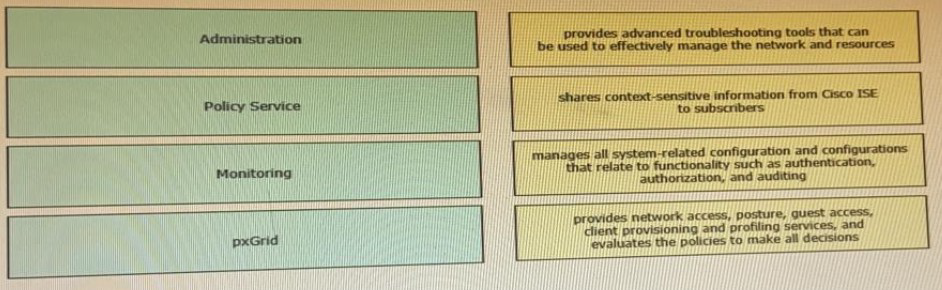
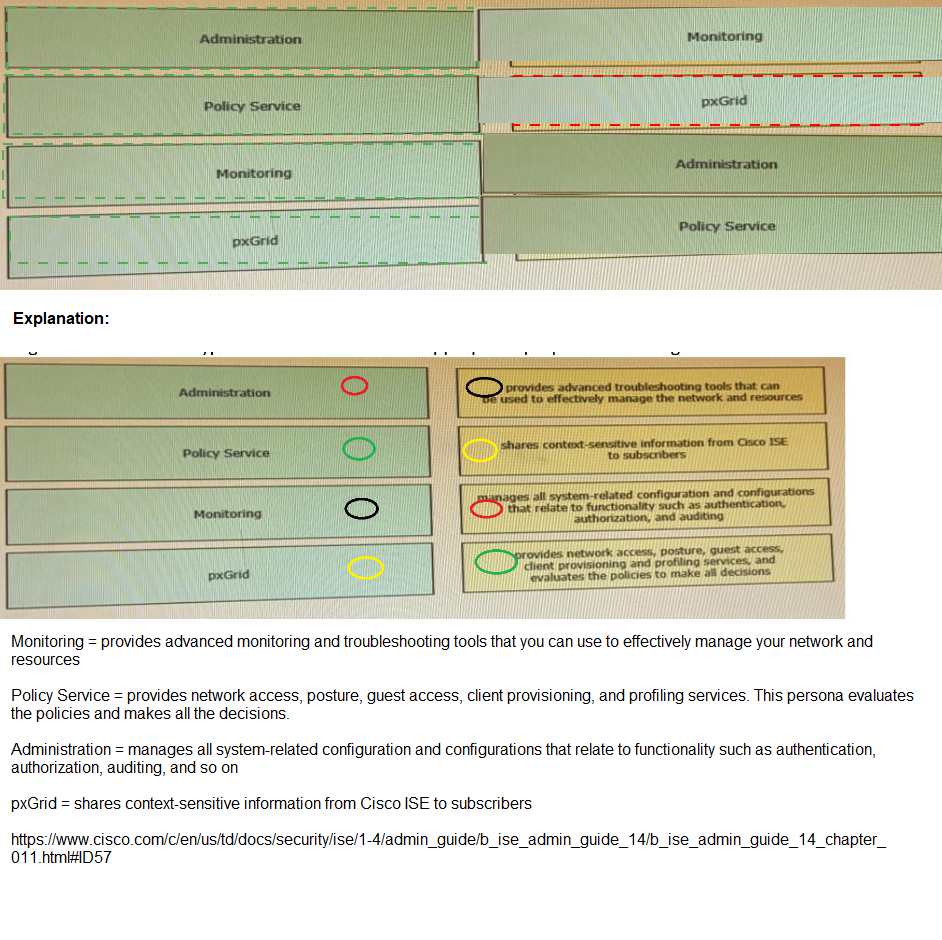
Which two components are required for creating a Native Supplicant Profile within a BYOD flow? (Choose two )
A.
Windows Settings
B.
Connection Type
C.
iOS Settings
D.
Redirect ACL
E.
Operating System
iOS Settings
Operating System
Which two ports must be open between Cisco ISE and the client when you configure posture on Cisco ISE? (Choose two).
A.
TCP 8443
B.
TCP 8906
C.
TCP 443
D.
TCP 80
E.
TCP 8905
TCP 80
TCP 8905
Which two features must be used on Cisco ISE to enable the TACACS. feature? (Choose two)
A.
Device Administration License
B.
Server Sequence
C.
Command Sets
D.
Enable Device Admin Service
E.
External TACACS Servers
Device Administration License
Enable Device Admin Service
Which supplicant(s) and server(s) are capable of supporting EAP-CHAINING?
A.
Cisco AnyConnect NAM and Cisco Identity Service Engine
B.
Cisco AnyConnect NAM and Cisco Access Control Server
C.
Cisco Secure Services Client and Cisco Access Control Server
D.
Windows Native Supplicant and Cisco Identity Service Engine
Cisco AnyConnect NAM and Cisco Identity Service Engine
Which advanced option within a WLAN must be enabled to trigger Central Web Authentication for Wireless users on AireOS controller?
A.
DHCP server
B.
static IP tunneling
C.
override Interface ACL
D.
AAA override
DHCP server
| Page 3 out of 20 Pages |
| Previous |