A corporation has a wireless network where all access points are configured in
FlexConnect. The WLC has a Data WLAN and a VoWiFi WLAN implemented where
centrally-switched is configured for the APs. Which QoS configuration must be
implemented for the wireless packets to maintain the marking across the wired and
wireless network?
A.
Enable CAC
B.
Trust DSCP
C.
Set QoS to Platinum
D.
Allow WMM
Trust DSCP
During the EAP process and specifically related to the client authentication session, which
encrypted key is sent from the RADIUS server to the access point?
A.
WPA key
B.
session key
C.
encryption key
D.
shared-secret key
session key
What is configured to use more than one port on the OEAP to extend the wired network's?
A.
AAA override
B.
client load balancing
C.
remote LAN ACL
D.
remote LAN
remote LAN
Refer to the exhibit.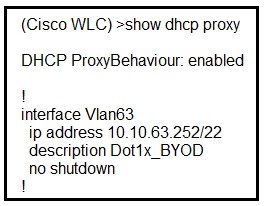
A network administrator deploys the DHCP profiler service in two ISE servers: 10.3.10.101
and 10.3.10.102. All BYOD devices connecting to WLAN on VLAN63 have been incorrectly
profiled and are assigned as unknown profiled endpoints. Which action efficiently rectifies
the issue according to Cisco recommendations?
A.
Nothing needed to be added on the Cisco WLC or VLAN interface. The ISE
configuration must be fixed.
B.
Disable DHCP proxy on the Cisco WLC.
C.
Disable DHCP proxy on the Cisco WLC and run the ip helper-address command under
the VLAN interface to point to DHCP and the two ISE servers.
D.
Keep DHCP proxy enabled on the Cisco WLC and define helper-address under the
VLAN interface to point to the two ISE servers.
Disable DHCP proxy on the Cisco WLC and run the ip helper-address command under
the VLAN interface to point to DHCP and the two ISE servers.
Explanation: https://www.cisco.com/c/en/us/support/docs/wireless/4400-series-wirelesslan-
controllers/110865-dhcp-wlc.html
When implementing self-registration for guest/BYOD devices, what happens when an
employee tries to connect four devices to the network at the same time?
A.
The last device is removed and the newly added device is updated as active device.
B.
The registration is allowed, but only one device is connected at any given time.
C.
All devices are allowed on the network simultaneously.
D.
Purge time dictates how long a device is registered to the portal
The registration is allowed, but only one device is connected at any given time.
Explanation:
https://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/Borderless_Networks/Unified_A
ccess/BYOD_Design_Guide/BYOD_Enhanced_Use_Case.html
Which devices can be tracked with the Cisco Context Aware Services?
A.
wired and wireless devices
B.
wireless devices
C.
wired devices
D.
Cisco certified wireless devices
wired and wireless devices
What is the default NMSP echo interval between Cisco MSE and a Wireless LAN
Controller?
A.
10 seconds
B.
15 seconds
C.
30 seconds
D.
60 seconds
15 seconds
Where is a Cisco OEAP enabled on a Cisco Catalyst 9800 Series Wireless Controller?
A.
RF Profile
B.
Flex Profile
C.
Policy Profile
D.
AP Join Profile
Flex Profile
An engineer configures a Cisco Aironet 600 Series OfficeExtend AP for a user who works
remotely. What is configured on the Cisco WLC to allow the user to print a printer on his
home network?
A.
split tunneling
B.
SE-connect
C.
FlexConnect
D.
AP failover priority
split tunneling
An engineer must configure a Cisco WLC to support Cisco Aironet 600 Series OfficeExtend
APs. Which two Layer 2 security options are supported in this environment? (Choose two.)
A.
Static WEP + 802.1X
B.
WPA+WPA2
C.
Static WEP
D.
CKIP
E.
802.1X
WPA+WPA2
Static WEP
A corporation has recently implemented a BYOD policy at their HQ. Which two risks should
the security director be concerned about? (Choose two.)
A.
network analyzers
B.
malware
C.
lost and stolen devices
D.
keyloggers
E.
unauthorized users
malware
lost and stolen devices
Explanation: https://ccbtechnology.com/byod-5-biggest-security-risks/
https://blogs.cisco.com/security/byod-many-call-it-bring-your-own-malware-byom
An engineer must create an account to log in to the CLI of an access point for
troubleshooting. Which configuration on the WLC will accomplish this?
A.
ReadWrite User Access Mode
B.
Global Configuration Enable Password
C.
SNMP V3 User
D.
Allow New Telnet Sessions
https://www.cisco.com/c/en/us/td/docs/wireless/controller/7-
4/configuration/guides/consolidated/b_cg74_CONSOLIDATED/b_cg74_CONSOLIDATED_
chapter_01101011.html
Global Configuration Enable Password
| Page 2 out of 7 Pages |
| Previous |