Topic 1: Exam Pool A
A user reports that a PC seems to be running more slowly than usual. A technician checks system resources, but disk, CPU, and memory usage seem to be fine. The technician sees that GPU temperature is extremely high. Which of the following types of malware is MOST likely to blame?
A. Spyware
B. Cryptominer
C. Ransormvare
D. Boot sector virus
Explanation:
The type of malware that is most likely to blame for a PC running more slowly than usual
and having an extremely high GPU temperature is a “cryptominer”. Cryptominers are a type
of malware that use the resources of a computer to mine cryptocurrency. This can cause
the computer to run more slowly than usual and can cause the GPU temperature to rise.
Spyware is a type of malware that is used to spy on a user’s activities, but it does not
typically cause high GPU temperatures. Ransomware is a type of malware that encrypts a
user’s files and demands payment to unlock them, but it does not typically cause high GPU
temperatures. Boot sector viruses are a type of malware that infects the boot sector of a
hard drive, but they do not typically cause high GPU temperatures12.
A technician has been tasked with installing a workstation that will be used tor point-of-sale transactions. The point-of-sale system will process credit cards and loyalty cards. Which of the following encryption technologies should be used to secure the workstation in case of theft?
A. Data-in-transit encryption
B. File encryption
C. USB drive encryption
D. Disk encryption
Explanation:
Disk encryption should be used to secure the workstation in case of theft. Disk encryption
can help to protect data on the hard drive by encrypting it so that it cannot be accessed
without the correct encryption key.
A technician wants to enable BitLocker on a Windows 10 laptop and is unable to find the BitLocker Drive Encryption menu item in Control Panel. Which of the following explains why the technician unable to find this menu item?
A. The hardware does not meet BitLocker's minimum system requirements.
B. BitLocker was renamed for Windows 10.
C. BitLocker is not included on Windows 10 Home.
D. BitLocker was disabled in the registry of the laptop
Explanation:
BitLocker is only available on Windows 10 Pro, Enterprise, and Education
editions1. Therefore, the technician is unable to find the BitLocker Drive Encryption menu
item in Control Panel because it is not included in the Windows 10 Home edition1.
A Windows computer is experiencing slow performance when the user tries to open programs and files. The user recently installed a new software program from an external website. Various websites are being redirected to an unauthorized site, and Task Manager shows the CPU usage is consistently at 100%. Which of the following should the technician do first?
A. Uninstall the new program.
B. Check the HOSTS file.
C. Restore from a previous backup.
D. Clear the web browser cache.
An Android user contacts the help desk because a company smartphone failed to complete a tethered OS update A technician determines there are no error messages on the device Which of the following should the technician do NEXT?
A. Verify all third-party applications are disabled
B. Determine if the device has adequate storage available.
C. Check if the battery is sufficiently charged
D. Confirm a strong internet connection is available using Wi-Fi or cellular data
Explanation:
Since there are no error messages on the device, the technician should check if the battery
is sufficiently charged1
If the battery is low, the device may not have enough power to complete the update2
In this scenario, the technician has already determined that there are no error messages on
the device. The next best step would be to check if the battery is sufficiently charged. If the
battery is low, it could be preventing the device from completing the update process.
Verifying that third-party applications are disabled, determining if the device has adequate
storage available, and confirming a strong internet connection are all important steps in
troubleshooting issues with mobile devices. However, since the problem in this scenario is
related to a failed OS update, it is important to first check the battery level before
proceeding with further troubleshooting steps.
Which of the following would typically require the most computing resources from the host computer? Chrome OS
A. Windows
B. Android
C. macOS
D. Linux
Explanation: Windows is the operating system that typically requires the most computing resources from the host computer, compared to the other options. Computing resources include hardware components such as CPU, RAM, disk space, graphics card, and network adapter. The minimum system requirements for an operating system indicate the minimum amount of computing resources needed to install and run the operating system on a computer. The higher the minimum system requirements, the more computing resources the operating system consumes. According to the web search results, the minimum system requirements for Windows 10 and Windows 11 are as follows12: CPU: 1 GHz or faster with two or more cores (Windows 10); 1 GHz or faster with two or more cores on a compatible 64-bit processor (Windows 11) RAM: 1 GB for 32-bit or 2 GB for 64-bit (Windows 10); 4 GB (Windows 11) Disk space: 16 GB for 32-bit or 32 GB for 64-bit (Windows 10); 64 GB (Windows 11) Graphics card: DirectX 9 or later with WDDM 1.0 driver (Windows 10); DirectX 12 compatible with WDDM 2.0 driver (Windows 11)
An architecture firm is considering upgrading its computer-aided design (CAD) software to the newest version that forces storage of backups of all CAD files on the software's cloud server. Which of the following is MOST likely to be of concern to the IT manager?
A. All updated software must be tested with alt system types and accessories
B. Extra technician hours must be budgeted during installation of updates
C. Network utilization will be significantly increased due to the size of CAD files
D. Large update and installation files will overload the local hard drives.
Explanation:
The IT manager is most likely to be concerned about network utilization being significantly
increased due to the size of CAD files. Backing up all CAD files to the software’s cloud server can result in a large amount of data being transferred over the network, which can
cause network congestion and slow down other network traffic.
The Chief Executive Officer at a bark recently saw a news report about a high-profile cybercrime where a remote-access tool that the bank uses for support was also used in this crime. The report stated that attackers were able to brute force passwords to access systems. Which of the following would BEST limit the bark's risk? (Select TWO)
A. Enable multifactor authentication for each support account
B. Limit remote access to destinations inside the corporate network
C. Block all support accounts from logging in from foreign countries
D. Configure a replacement remote-access tool for support cases.
E. Purchase a password manager for remote-access tool users
F. Enforce account lockouts after five bad password attempts
Explanation:
The best ways to limit the bank’s risk are to enable multifactor authentication for each
support account and enforce account lockouts after five bad password attempts. Multifactor
authentication adds an extra layer of security to the login process, making it more difficult
for attackers to gain access to systems. Account lockouts after five bad password attempts
can help to prevent brute force attacks by locking out accounts after a certain number of
failed login attempts.
A technician is trying to connect to a user's laptop in order to securely install updates. Given the following information about the laptop:
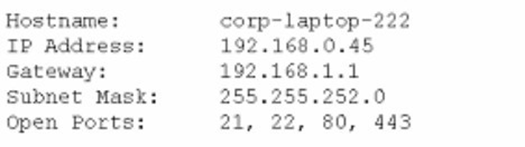
Which of the following should the technician do to connect via RDP?
A. Confirm the user can ping the default gateway.
B. Change the IP address on the user's laptop.
C. Change the subnet mask on the user's laptop.
D. Open port 3389 on the Windows firewall.
A user reports that text on the screen is too small. The user would like to make the text larger and easier to see. Which of the following is the BEST way for the user to increase the size of text, applications, and other items using the Windows 10 Settings tool?
A. Open Settings select Devices, select Display, and change the display resolution to a lower resolution option
B. Open Settings, select System, select Display, and change the display resolution to a lower resolution option.
C. Open Settings Select System, select Display, and change the Scale and layout setting to a higher percentage
D. Open Settings select Personalization, select Display and change the Scale and layout setting to a higher percentage
Explanation:
Open Settings, select System, select Display, and change the Scale and layout setting to a
higher percentage123
Reference: 4. How to Increase the Text Size on Your Computer. Retrieved from
https://www.laptopmag.com/articles/increase-text-size-computer 5. How to Change the
Size of Text in Windows 10.
Retrieved from https://www.howtogeek.com/370055/how-tochange-
the-size-of-text-in-windows-10/ 6. Change the size of text in Windows.
Retrieved
from https://support.microsoft.com/en-us/windows/change-the-size-of-text-in-windows-
1d5830c3-eee3-8eaa-836b-abcc37d99b9a
A technician needs to reimage a desktop in an area without network access. Which of the following should the technician use? (Select two).
A. USB
B. PXE
C. Optical media
D. Partition
E. Boot record
F. SMB
Explanation: A technician needs to reimage a desktop in an area without network access, which means that the technician cannot use network-based methods such as PXE or SMB to deploy the image. Therefore, the technician should use offline methods that involve removable media such as USB or optical media. USB and optical media are common ways to store and transfer system images, and they can be used to boot the desktop and initiate the reimaging process. The technician will need to create a bootable USB or optical media that contains the system image and the imaging software, and then insert it into the desktop and change the boot order in the BIOS or UEFI settings. The technician can then follow the instructions on the screen to reimage the desktop
Welcome to your first day as a Fictional Company. LLC helpdesk employee. Please work
the tickets in your helpdesk ticket queue.
Click on individual tickers to see the ticket details. View attachments to determine the
problem.
Select the appropriate issue from the 'issue' drop-down menu. Then, select the MOST
efficient resolution from the 'Resolution' drop-down menu. Finally, select the proper
command or verification to remediate or confirm your fix of the issue from the Verify
Resolve drop-down menu.


| Page 7 out of 62 Pages |
| Previous |