Topic 5: Exam Pool E
A computer technician is investigating a computer that is not booting. The user reports that the computer was working prior to shutting it down last night. The technician notices a removable USB device is inserted, and the user explains the device is a prize the user received in the mail yesterday. Which of the following types of attacks does this describe?
A. Phishing
B. Dumpster diving
C. Tailgating
D. Evil twin
A technician is unable to join a Windows 10 laptop to a domain Which of the following is the MOST likely reason?
A. The domain's processor compatibility is not met
B. The laptop has Windows 10 Home installed
C. The laptop does not have an onboard Ethernet adapter
D. The Laptop does not have all current Windows updates installed
A change advisory board did not approve a requested change due to the lack of alternative actions if implementation failed. Which of the following should be updated before requesting approval again?
A. Scope of change
B. Risk level
C. Rollback plan
D. End user acceptance
Explanation:
The rollback plan should be updated before requesting approval again. A rollback plan is a
plan for undoing a change if it causes problems, and it is an important part of any change
management process. If the change advisory board did not approve the requested change
due to the lack of alternative actions if implementation failed, then updating the rollback
plan would be the best way to address this concern.
A technician is installing software on a user's workstation. The installation fails due to incompliance with the HCL. Which of the following components is most likely causing the installation to fail? (Select two).
A. NIC
B. CPU
C. PSU
D. KVM
E. RAM
F. DVI
Explanation: The Hardware Compatibility List (HCL) is a list that indicates hardware components that are compatible with a specific software or operating system. If software installation fails due to incompliance with the HCL, it's most likely due to core hardware components like the Network Interface Card (NIC) or the Central Processing Unit (CPU) not being supported or not meeting the software's minimum hardware requirements. The PSU, KVM, RAM, and DVI are less likely to directly impact software compatibility as defined by the HCL.
A user is experiencing frequent malware symptoms on a Windows workstation. The user has tried several times to roll back the state but the malware persists. Which of the following would MOST likely resolve the issue?
A. Quarantining system files
B. Reimaging the workstation
C. Encrypting the hard drive
D. Disabling TLS 1.0 support
Explanation:
Encrypting the hard drive would most likely resolve the issue.
Following the latest Windows update PDF files are opening in Microsoft Edge instead of Adobe Reader. Which of the following utilities should be used to ensure all PDF files open in Adobe Reader?
A. Network and Sharing Center
B. Programs and Features
C. Default Apps
D. Add or Remove Programs
Explanation:
Default Apps should be used to ensure all PDF files open in Adobe Reader.
A technician has spent hours trying to resolve a computer issue for the company's Chief Executive Officer (CEO). The CEO needs the device returned as soon as possible. Which of the following steps should the technician take NEXT?
A. Continue researching the issue
B. Repeat the iterative processes
C. Inform the CEO the repair will take a couple of weeks
D. Escalate the ticket
Explanation:
The technician should escalate the ticket to ensure that the CEO’s device is returned as
soon as possible.
An organization is centralizing support functions and requires the ability to support a remote user's desktop. Which of the following technologies will allow a technician to see the issue along with the user?
A. RDP
B. VNC
C. SSH
D. VPN
Explanation:
VNC will allow a technician to see the issue along with the user when an organization is
centralizing support functions and requires the ability to support a remote user’s desktop.
Which of the following must be maintained throughout the forensic evidence life cycle when dealing with a piece of evidence?
A. Acceptable use
B. Chain of custody
C. Security policy
D. Information management
Explanation:
The aspect of forensic evidence life cycle that must be maintained when dealing with a
piece of evidence is chain of custody. This is because chain of custody is the
documentation of the movement of evidence from the time it is collected to the time it is
presented in court, and it is important to maintain the integrity of the evidence.
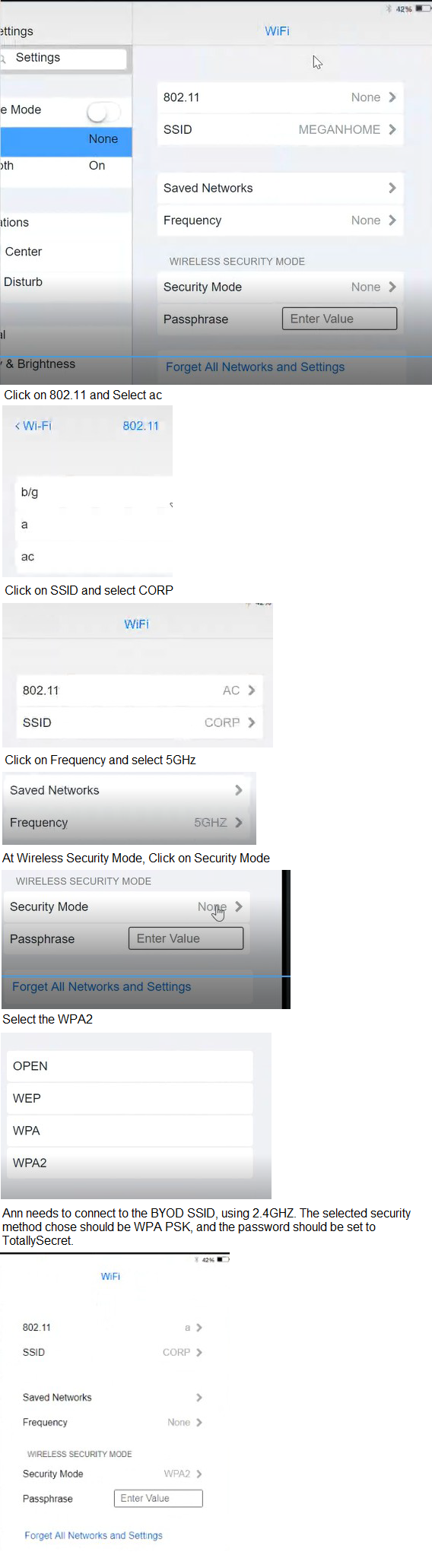
Ann, a CEO, has purchased a new consumer-class tablet for personal use, but she is
unable to connect it to the company’s wireless network. All the corporate laptops are
connecting without issue. She has asked you to assist with getting the device online.
A technician suspects a rootkit has been installed and needs to be removed. Which of the following would BEST resolve the issue?
A. Application updates
B. Anti-malware software
C. OS reinstallation
D. File restore
Explanation:
If a rootkit has caused a deep infection, then the only way to remove the rootkit is to
reinstall the operating system. This is because rootkits are designed to be difficult to detect
and remove, and they can hide in the operating system’s kernel, making it difficult to
remove them without reinstalling the operating system.
A customer service representative is unable to send jobs to a printer at a remote branch office. However, the representative can print successfully to a local network printer. Which of the following commands should a technician use to view the path of the network traffic from the PC?
A. netstat
B. ping
C. format
D. tracert
Explanation: The "tracert" command is used to view the path that network traffic takes from a PC to a specified destination. It is helpful in identifying where along the path the traffic may be failing or experiencing delays. In the scenario where a customer service representative can't send jobs to a remote printer but can print locally, "tracert" can help diagnose if there's a network routing issue affecting the connection to the remote branch office.
| Page 17 out of 62 Pages |
| Previous |