Topic 1: Exam Pool A
A user wants to set up speech recognition on a PC. In which of the following Windows Settings tools can the user enable this option?
A. Language
B. System
C. Personalization
D. Ease of Access
Explanation:
The user can enable speech recognition on a PC in the Ease of Access settings tool. To
set up Speech Recognition on a Windows PC, the user should open Control Panel, click on
Ease of Access, click on Speech Recognition, and click the Start Speech Recognition link.
Language settings can be used to change the language of the speech recognition feature,
but they will not enable the feature. System settings can be used to configure the hardware
and software of the PC, but they will not enable the speech recognition
feature. Personalization settings can be used to customize the appearance and behavior of
the PC, but they will not enable the speech recognition feature1. Open up ease of access, click on speech, then there is an on and off button for speech
recognition.
After a security event, a technician removes malware from an affected laptop and disconnects the laptop from the network. Which of the following should the technician do to prevent the operating system from automatically returning to an infected state?
A. Enable System Restore.
B. Disable System Restore.
C. Enable antivirus.
D. Disable antivirus.
E. Educate the user.
Explanation: System Restore is a feature that allows the user to revert the system to a previous state. However, this can also restore the malware that was removed by the technician. Disabling System Restore can prevent the operating system from automatically returning to an infected state. Enabling antivirus, educating the user, and enabling System Restore are good preventive measures, but they do not address the question. Disabling antivirus can make the system more vulnerable to malware attacks
A user reports a computer is running slow. Which of the following tools will help a technician identify the issue?
A. Disk Cleanup
B. Group Policy Editor
C. Disk Management
D. Resource Monitor
Explanation:
Resource Monitor is a Windows utility that can be used to monitor and analyze the system
resources and processes running on a computer. It can be used to identify and
troubleshoot any issues that might be causing the computer to run slowly, such as CPU
usage, memory usage, disk I/O, and network usage.
A student is setting up a new Windows 10 laptop for the upcoming semester. The student is interested in customizing the wallpaper. Which of the following should the student use to change the wallpaper?
A. Apps and Features
B. Personalization
C. File Explorer
D. Task Manager
Explanation: To change the wallpaper on a Windows 10 laptop, the "Personalization" settings should be used. These settings allow users to customize themes, which include various aspects of the desktop environment such as the desktop wallpaper, screen saver, color scheme, and more. This makes "Personalization" the correct option for customizing the wallpaper.References: Official CompTIA A+ Core 1 and Core 2 Student Guide.
A user requested that the file permissions on a Linux device be changed to only allow access to a certain group of users. Which of the following commands should be used to complete the user's request?
A. cat
B. chmod
C. pwd
D. cacls
After clicking on a link in an email a Chief Financial Officer (CFO) received the following
error:
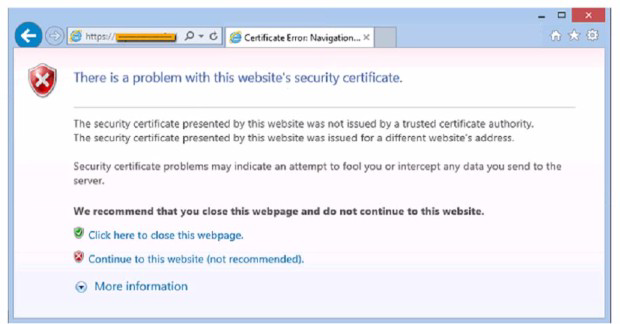
A. Update the browser's CRLs
B. File a trouble ticket with the bank.
C. Contact the ISP to report the CFCs concern
D. Instruct the CFO to exit the browser
Explanation:
The technician should update the browser’s CRLs first. The error message indicates that
the certificate revocation list (CRL) is not up to date. Updating the CRLs will ensure that the
browser can verify the authenticity of the bank’s website.
A technician has verified that a user's computer has a virus and the antivirus software is out of date. Which of the following steps should the technician take next?
A. Quarantine the computer.
B. Use a previous restore point.
C. Educate the end user about viruses.
D. Download the latest virus definitions.
A technician needs to replace a PC's motherboard. The technician shuts down the PC. Which of the following steps should the technician take next?
A. Turn off the monitor.
B. Remove the power cord.
C. Remove the PSU.
D. Remove the RAM modules.
Explanation: Removing the power cord is the first step to ensure the safety of the technician and the PC components. This will prevent any electrical shock or damage that may occur if the PC is still connected to a power source. The technician should also press the power button to drain any residual power from the capacitors.
A technician is modifying the default home page of all the workstations in a company. Which of the following will help to implement this change?
A. Group Policy
B. Browser extension
C. System Configuration
D. Task Scheduler
Explanation: Group Policy is a feature of Windows that allows administrators to centrally manage and configure the settings of computers and users in a domain network. Group Policy can be used to modify the default home page of all the workstations in a company by creating and applying a policy that specifies the desired URL for the home page. This way, the change will be automatically applied to all the workstations that are joined to the domain and receive the policy.
A user attempts to open some files, but a message appears stating that the files are encrypted. The user was able to access these files before without receiving this message and no changes have been made within the company. Which of the following has infected the computer?
A. Cryptominer
B. Phishing
C. Ransomware
D. Keylogger
Explanation:
Ransomware is malicious software that encrypts files on a computer, making them
inaccessible until a ransom is paid. In this case, the user was able to access the files
before without issue, and no changes have been made within the company, so it is likely
that the computer was infected with ransomware.
A help desk technician is troubleshooting a workstation in a SOHO environment that is running above normal system baselines. The technician discovers an unknown executable with a random string name running on the system. The technician terminates the process, and the system returns to normal operation. The technician thinks the issue was an infected file, but the antivirus is not detecting a threat. The technician is concerned other machines may be infected with this unknown virus. Which of the following is the MOST effective way to check other machines on the network for this unknown threat?
A. Run a startup script that removes files by name.
B. Provide a sample to the antivirus vendor
C. Manually check each machine.
D. Monitor outbound network traffic.
Explanation:
The most effective way to check other machines on the network for this unknown threat is
to manually check each machine. This can help to identify any other machines that may be
infected with the unknown virus and allow them to be cleaned.
When a user is in the office, the user's mobile phone loads applications and web browses very slowly on a cellular connection. Which of the following is the best way to fix this issue? Connect to the company's Wi-Fi network.
A. Change the settings on the phone to connect to a different cellular tower.
B. Install a cellular repeater at the office for this user.
C. Update all applications on the phone.
| Page 11 out of 62 Pages |
| Previous |