Topic 5: Exam Pool E (NEW)
Which of the following cables provides the best performance with the least EMI?
A. Cat 5
B. Cat 6
C. Cat 7
D. Coaxial
Explanation: Category 7 (Cat 7) cables provide the best performance with the least Electromagnetic Interference (EMI) due to their enhanced shielding. Cat 7 cables are designed to support higher speeds and bandwidth while reducing interference compared to Cat 5 or Cat 6.
✑ Why Not A (Cat 5): Cat 5 cables have limited shielding and are prone to EMI,
making them unsuitable for high-performance requirements.
✑ Why Not B (Cat 6): Cat 6 offers better shielding than Cat 5 but less than Cat 7.
✑ Why Not D (Coaxial): While coaxial cables are resistant to EMI, Cat 7 offers better performance overall for networking applications.
CompTIA A+ Exam Reference: Core 1 (220-1101), Section 3.1, cable types and their performance characteristics.
After an IT department implements SSL redirection, users report being unable to access a random number generator opened within a web browser. Which of the following should a technician do first to troubleshoot this issue?
A. Ensure that the computer supports secure socket communication.
B. Report the affected user accounts to the IT department.
C. Reset the web browser cache.
D. Check to see whether the website is HTTPS enabled.
Which of the following standards supports MIMO technology?
A. 802.11a
B. 802.11b
C. 802.11g
D. 802.11n
Explanation: The 802.11n wireless networking standard supports Multiple Input Multiple Output (MIMO) technology. MIMO technology uses multiple antennas on both the transmitting and receiving devices to improve wireless performance by increasing the amount of data that can be transmitted simultaneously. 802.11a, 802.11b, and 802.11g do not support MIMO technology. References: CompTIA A+ Certification Exam: Core 1 - Objective 3.3
An IT manager discovered that hundreds of pages of printed materials are being recycled each day because the materials are left on the printer tray instead of being picked up by users. Which of the following would BEST prevent this waste?
A. Send friendly reminders to not print unnecessarily
B. Enable duplex printing to reduce paper utilization
C. Bill each department for the excess material cost
D. Require a code or badge before releasing a print job
Explanation: By requiring a code or badge before releasing a print job, it ensures that only
authorized personnel can collect the printouts. This method is effective in preventing waste
and in keeping sensitive documents confidential. Sending reminders, enabling duplex
printing, and billing departments are useful strategies for reducing paper utilization but may
not necessarily prevent waste caused by uncollected printouts.
Requiring a code or badge before releasing a print job is the best solution to prevent the
waste of printed materials, as it ensures that only the user who initiated the print job is able
to pick up the printed materials. This can be achieved by implementing print release
software or requiring users to enter a PIN code at the printer. References: CompTIA A+
Certification Exam Objectives 1001, 2.10
A user brings an older laptop to the help desk and reports issues with the keyboard. Upon inspection, the technician does not see any external damage but notices that many keystrokes da not register in a word processor. The laptop works fine when the technician tests it with an external keyboard. Which of the following actions would MOST likely resolve the issue?
A. Disable the sticky keys feature.
B. Clean the keyboard
C. Reset the BIOS settings to default.
D. Charge the laptop.
Explanation: The most likely action that would resolve the issue is to clean the keyboard. Sometimes dust, hair, and other debris can affect keyboard functionality. The technician can try to clean the keyboard as much as possible, which may be enough to get the keyboard back in working order.
A company wants to use client-side visualization for application testing. Which of the following configurations would BEST support this goal?
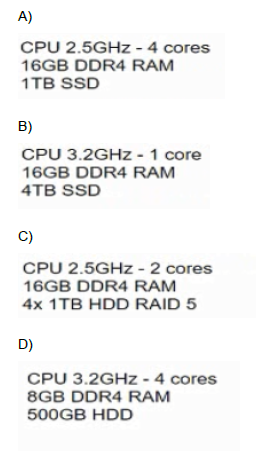
A. Option A
B. Option B
C. Option C
D. Option D
A user's computer is not receiving a network connection. The technician confirms that the connection seems to be down and looks for the user's port on the patch panel. The port and patch panel are not labeled. Which of the following network tools should the technician use to identify the port?
A. Network tap
B. Punchdown tool
C. Toner probe
D. Crimper
Explanation: Toner Probe Many cable testers also incorporate the function of a toner probe, which is used to identify a cable from within a bundle. This may be necessary when the cables have not been labeled properly. The tone generator is connected to the cable using an RJ45 jack and applies a continuous audio signal on the cable. The probe is used to detect the signal and follow the cable over ceilings and through ducts or identify it from within the rest of the bundle.
A laptop's external webcam software is running, but it shows no image or video. Which of the following should a technician perform FIRST?
A. Research new webcam firmware
B. Restart the computer and run system diagnostics
C. Reseat the webcam.
D. Reinstall the webcam software and drivers.
Explanation: https://www.lifewire.com/fix-it-when-webcam-is-not-working-4588517 If a laptop's external webcam software is running, but it shows no image or video, the first step the technician should perform is to reseat the webcam. Reseating the webcam involves disconnecting it from the motherboard and then reconnecting it. If this doesn't work, the technician should then check the webcam drivers or software. References: CompTIA A+ Certification All-in-One Exam Guide, Tenth Edition by Mike Meyers (Page 502)
Upon booting a workstation, a technician hears a distinct clicking sound after power is applied to the motherboard. Which of the following would MOST likely be the cause?
A. RAID
B. SSD
C. S.M.A.R.T
D. HDD
Explanation: The clicking sound is the sound of a damaged disk in the HDD A clicking sound from a hard disk drive typically indicates a mechanical failure, such as the read/write head hitting a physical obstruction or a problem with the disk motor. This can cause the drive to fail to initialize or not be recognized by the system during booting.
A user submits a help desk ticket regarding a smartphone that will no longer accept its charging cable. The assigned technician notices the phone does not have a protective case, and the user constantly transport the phone in a pocket. The technician attempts to use a secondary charger, but the cable falls out of the phone. Which of the following is the MOST likely cause of the issue?
A. The phone requires a firmware update to address charging issues.
B. The charge port contains foreign objects, such as lint.
C. The phone’s battery has swelled, preventing the utilization of the charge port.
D. The phone has experienced water damage, thus the battery is not charring.
Explanation: The symptoms suggest that the charging cable falls out of the phone, indicating that the charge port may contain foreign objects such as lint, which can interfere with the connection between the charging cable and the phone.
A developer is requesting permission to utilize client-side visualization. The developer would like to write code in a setting isolated from other infrastructure to avoid negative impacts of experimental code. Which of the following provides the BEST solution for the developer?
A. Cross-platform functionality
B. Software compatibility
C. Test case development
D. Sandbox environment
Explanation: A sandbox environment is an isolated testing environment where code can be written and tested without impacting other infrastructure. This provides a safe and controlled environment for experimentation and development.
An organization maintains various record types, including health and criminal justice records. Which of the following cloud environments is the organization MOST likely to use to limit the attack surface?
A. Public
B. Hybrid
C. Community
D. Private
Explanation: Private cloud environments are designed for use by a single organization and offer the greatest control over security and access to data. They are typically used for sensitive or confidential data, such as health and criminal justice records. Public cloud environments are shared by multiple organizations and offer less control over security and access to data. Hybrid cloud environments combine public and private clouds, while community clouds are shared by multiple organizations with similar needs. References: CompTIA A+ Certification Exam: Core 1 - Page 234
| Page 11 out of 71 Pages |
| Previous |