What is the purpose of the Cisco VIRL software tool?
A.
To verify configurations against compliance standards
B.
To simulate and model networks
C.
To automate API workflows
D.
To test performance of an application
To simulate and model networks
Refer to the exhibit

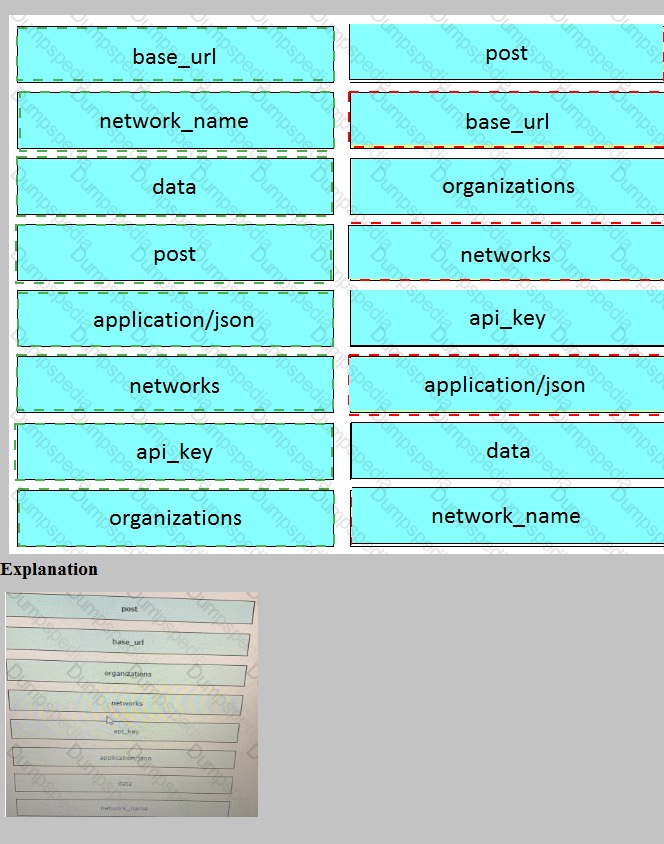
Which type of threat occur when an attacker can send hostile data to an interpreter within an application?
A.
Cross-site scripting
B.
Sensitive data exposure
C.
Broken authentication
D.
Injection
Injection
Which statement describes the benefit of using functions in programming?
A.
Functions allow problems to be split into simpler, smaller groups, and reduce code repetition, which makes the code easier to read.
B.
Functions ensure that a developer understands the inner logic contained before using them as part of a script or application.
C.
Functions create the implementation of secret and encrypted algorithms.
D.
Functions store mutable values within a script 01 application.
Functions allow problems to be split into simpler, smaller groups, and reduce code repetition, which makes the code easier to read.
What are two security benefits of a Docker-based application?
A.
easier to patch because Docker containers include only dependencies that the application requires
B.
prevents information leakage that can occur when unhandled exceptions are returned in HTTP responses
C.
allows for separation of application that traditionally run in the same host
D.
natively secures access to secrets that are used by the running application
E.
guarantees container images are secured and free of vulnerabilities
easier to patch because Docker containers include only dependencies that the application requires
allows for separation of application that traditionally run in the same host
Refer to the exhibit. 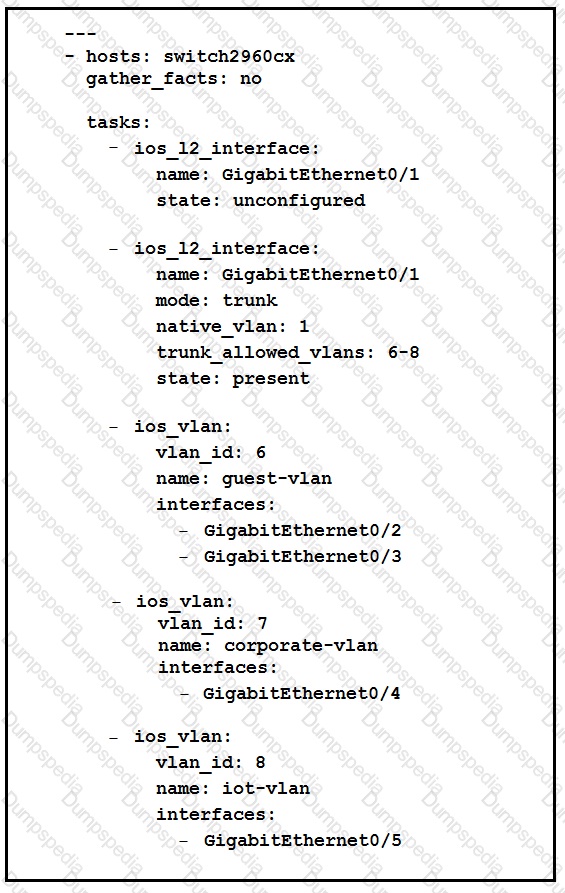
Which two statement describe the configuration of the Ansible script is run? (Choose two.)
A.
Traffic on port 0/2 and 0/3 is connected to port 0/6.
B.
Traffic from ports 0/2 to 0/5 can flow on port 0/1 due to the trunk.
C.
Traffic can flow between ports 0/2 to 0/5 due to the trunk on port 0/1.
D.
GigabitEthernet0/2 and GigabitEthernet0/3 are access ports for VLAN 6.
E.
GiabitEthernet0/1 is left unconfigured
Traffic from ports 0/2 to 0/5 can flow on port 0/1 due to the trunk.
GigabitEthernet0/2 and GigabitEthernet0/3 are access ports for VLAN 6.
Refer to the exhibit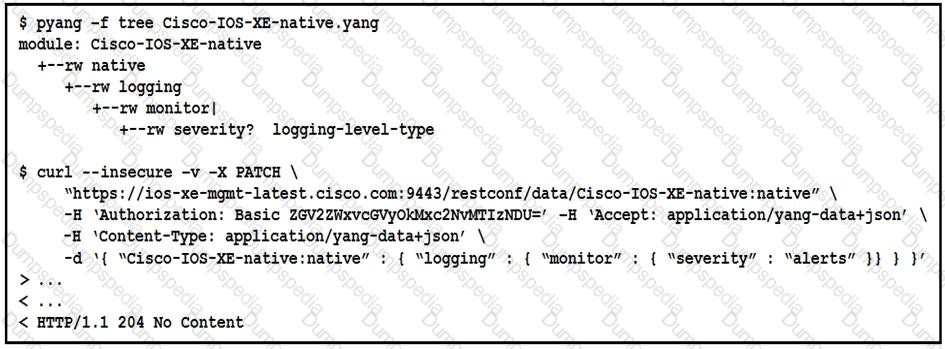
The definition of the YANG module and a RESTCONF query sent to a Cisco IOc XE device is shown. Which statement is correct if the RESTCONF interface responds with a 204 status code?
A.
The query failed at retrieving the logging seventy level.
B.
The query failed to set the logging seventy level due to an invalid path.
C.
The query retrieved the logging seventy level.
D.
The query updated the logging seventy level or created it if not present on the device
The query updated the logging seventy level or created it if not present on the device
Which description of a default gateway if true?
A.
It is a device that receives IP packets that have no explicit next-hop in the routing table.
B.
It is a feature that translates between public and private addresses.
C.
It is a security feature that denies certain traffic.
D.
It is a device that receives Layer 2 frames with an unknown destination address
It is a device that receives IP packets that have no explicit next-hop in the routing table.
https://www.certificationkits.com/cisco-certification/ccna-articles/cisco-ccna-intro-to-routing-basics/cisco-ccna-default
Refer to the exhibit.
Which python data structure does my_josn contain?
A.
List
B.
Json
C.
Map
D.
Dict
Dict
What are two benefit of managing network configuration via APIs? (Choose two.)
A.
configuration on devices becomes less complex
B.
more security due to locking out manual device configuration
C.
increased scalability and consistency of network changes
D.
eliminates the need of legacy management protocols like SNMP
E.
reduction in network changes performed manually
increased scalability and consistency of network changes
reduction in network changes performed manually
What is the outcome of executing this command?
git clone ssh://john@exmaple.com/path/to/my-project_git
A.
Creates a local copy of a repository called “my project”
B.
Creates a copy of a branch called “my project”
C.
Initiates a new Git repository called “my project”
D.
Creates a new branch called “my project”
Creates a local copy of a repository called “my project”
Which mechanism is used to consume a RESTful API design when large amounts of data are returned?
A.
Data sets
B.
Scrolling
C.
Blobs
D.
Pagination
Pagination
| Page 7 out of 18 Pages |
| Previous |