Topic 1: Exam Pool A
desc about topic
Refer to the exhibit.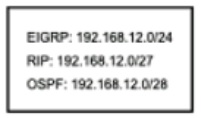
How does the router manage traffic to 192.168.12.16?
A.
It selects the RIP route because it has the longest prefix inclusive of the destination
address.
B.
It chooses the OSPF route because it has the longest prefix inclusive of the destination address.
C.
it load-balances traffic between all three routes
D.
It chooses the EIGRP route because it has the lowest administrative distance
It selects the RIP route because it has the longest prefix inclusive of the destination
address.
Which device performs stateful inspection of traffic?
A.
firewall
B.
switch
C.
access point
D.
wireless controller
firewall
Refer to the exhibit.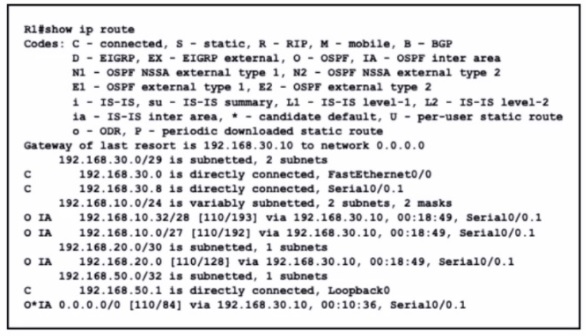
What is the metric of the route to the 192.168.10.33/28 subnet?
A.
84
B.
110
C.
128
D.
192
E.
193
193
Which spanning-tree enhancement avoids the learning and listening states and
immediately places ports in the forwarding state?
A.
BPDUfilter
B.
PortFast
C.
Backbonefast
D.
BPDUguard
PortFast
Explanation: PortFast
Spanning Tree Portfast causes layer 2 switch interfaces to enter forwarding state
immediately, bypassing the listening and learning states. It should be used on ports connected directly to end hosts like servers or workstations. Note: If portfast isn’t enabled,
DHCP timeouts can occur while STP converges, causing more problems.
https://skminhaj.wordpress.com/2015/03/04/spanning-tree-stp-rstp-mst-enhancements/
Refer to the exhibit.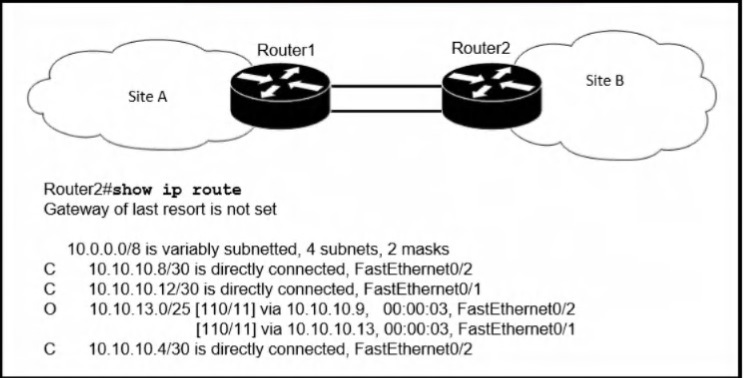
If OSPF Is running on this network, how does Router2 handle traffic from Site B to
10.10.13.128/25 at Site A?
A.
It load-balances traffic out of Fa0/1 and Fa0/2.
B.
It is unreachable and discards the traffic.
C.
It sends packets out of interface FaO/2.
D.
It sends packets out of interface Fa0/1.
It is unreachable and discards the traffic.
Refer to the exhibit.
A network administrator must permit SSH access to remotely manage routers in a network.
The operations team resides on the 10.20.1.0/25 network. Which command will accomplish
this task?
A.
access-list 2699 permit udp 10.20.1.0 0.0.0.255
B.
no access-list 2699 deny tcp any 10.20.1.0 0.0.0.127 eq 22
C.
access-list 2699 permit tcp any 10.20.1.0 0.0.0.255 eq 22
D.
no access-list 2699 deny ip any 10.20.1.0 0.0.0.255
no access-list 2699 deny ip any 10.20.1.0 0.0.0.255
Explanation: Note : Already a statement is there in last to allow SSH Traffic for network
10.20.1.0 0.0.0.127, but Second statement says deny ip any 10.20.1.0 0.0.0.255, so how it
will work once it is denied. So the right answer is remove the -- no access-list 2699 deny ip
any 10.20.1.0 0.0.0.255.
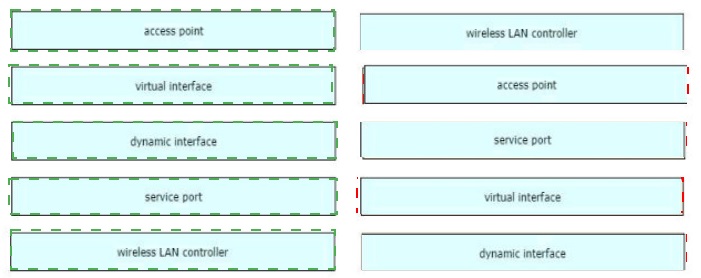
Drag and drop the WLAN components from the left onto the correct descriptions on the right.
Refer to the exhibit.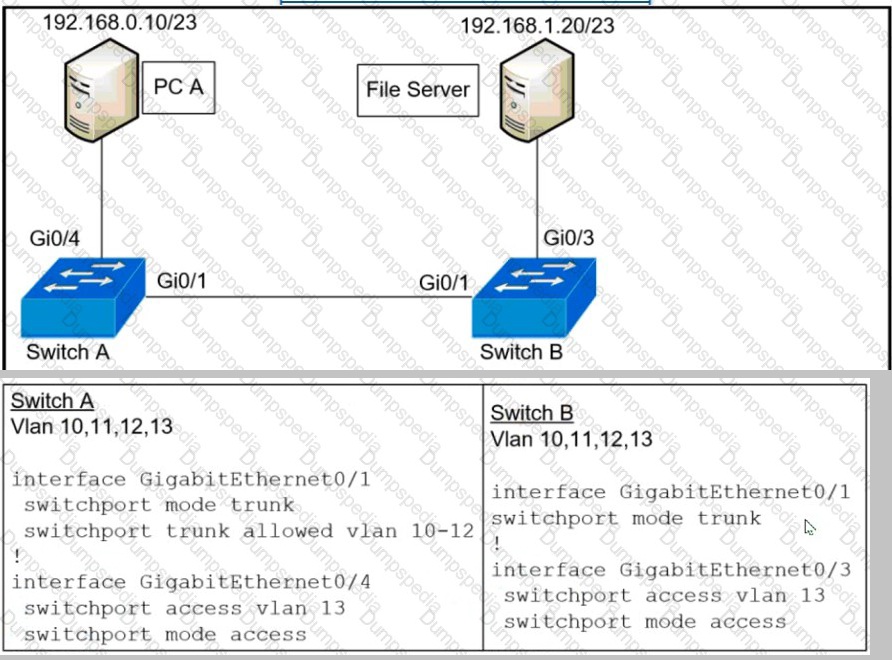
An extended ACL has been configured and applied to router R2 The configuration
failed to work as intended Which two
changes stop outbound traffic on TCP ports 25 and 80 to 10.0.20 0 26 from the
10.0.10 0/26 subnet while still allowing all other traffic? (Choose
two )
A.
Add a "permit ip any any" statement to the begining of ACL 101 for allowed traffic.
B.
Add a "permit ip any any" statement at the end of ACL 101 for allowed traffic
C.
The source and destination IPs must be swapped in ACL 101
D.
The ACL must be configured the Gi0/2 interface inbound on R1
E.
The ACL must be moved to the Gi0/1 interface outbound on R2
Add a "permit ip any any" statement at the end of ACL 101 for allowed traffic
The source and destination IPs must be swapped in ACL 101
How does HSRP provide first hop redundancy?
A.
It load-balances traffic by assigning the same metric value to more than one route to the
same destination m the IP routing table.
B.
It load-balances Layer 2 traffic along the path by flooding traffic out all interfaces
configured with the same VLAN.
C.
It forwards multiple packets to the same destination over different routed links n the data
path
D.
It uses a shared virtual MAC and a virtual IP address to a group of routers that serve as
the default gateway for hosts on a LAN
It uses a shared virtual MAC and a virtual IP address to a group of routers that serve as
the default gateway for hosts on a LAN
What is a function of a remote access VPN?
A.
used cryptographic tunneling to protect the privacy of data for multiple users
simultaneously
B.
used exclusively when a user is connected to a company's internal network
C.
establishes a secure tunnel between two branch sites
D.
allows the users to access company internal network resources through a secure tunnel
allows the users to access company internal network resources through a secure tunnel
An engineer is asked to protect unused ports that are configured in the default VLAN on a
switch.
Which two steps will fulfill the request? (Choose two)
A.
Configure the ports in an EtherChannel.
B.
Administratively shut down the ports
C.
Configure the port type as access and place in VLAN 99
D.
Configure the ports as trunk ports
E.
Enable the Cisco Discovery Protocol
Administratively shut down the ports
Configure the port type as access and place in VLAN 99
Which two events occur automatically when a device Is added to Cisco DNA Center? (Choose two. )
A.
The device Is assigned to the Global site.
B.
The device Is placed into the Unmanaged state.
C.
The device Is placed into the Provisioned state.
D.
The device Is placed into the Managed state.
E.
The device is assigned to the Local site.
The device Is assigned to the Global site.
The device Is placed into the Unmanaged state.
| Page 8 out of 72 Pages |
| Previous |