Topic 1: Exam Pool A
desc about topic
Refer to the exhibit.
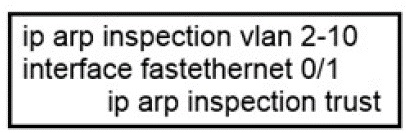
If the network environment is operating normally, which type of device must be connected
to interface FastEthernet 0/1?
A.
DHCP client
B.
access point
C.
router
D.
PC
router
Which HTTP status code is returned after a successful REST API request?
A.
200
B.
301
C.
404
D.
500
200
Which technology is appropriate for communication between an SDN controller and applications running over the network?
A.
OpenFlow
B.
REST API
C.
NETCONF
D.
Southbound API
REST API
What are two roles of the Dynamic Host Configuration Protocol (DHCP)? (Choose two)
A.
The DHCP server offers the ability to exclude specific IP addresses from a pool of IP
addresses
B.
The DHCP client can request up to four DNS server addresses
C.
The DHCP server assigns IP addresses without requiring the client to renew them
D.
The DHCP server leases client IP addresses dynamically.
E.
The DHCP client maintains a pool of IP addresses it can assign.
The DHCP server offers the ability to exclude specific IP addresses from a pool of IP
addresses
The DHCP server leases client IP addresses dynamically.
Refer to the exhibit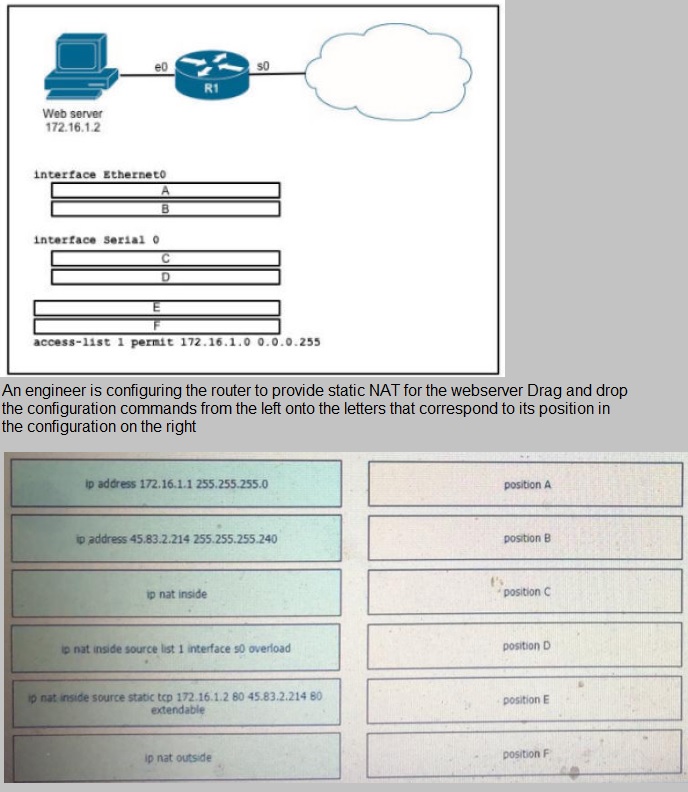
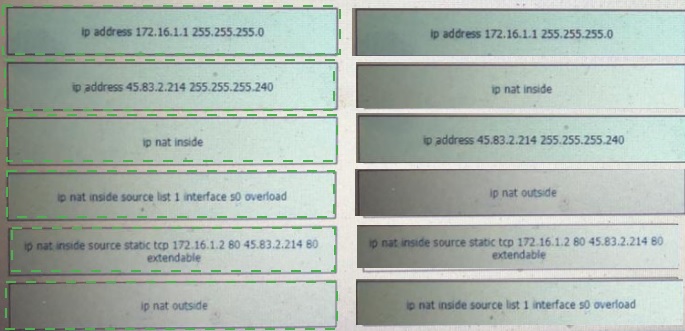
What does a switch use to build its MAC address table?
A.
VTP
B.
DTP
C.
egress traffic
D.
ingress traffic
ingress traffic
Which API is used in controller-based architectures to interact with edge devices?
A.
overlay
B.
northbound
C.
underlay
D.
southbound
southbound
Refer to the exhibit.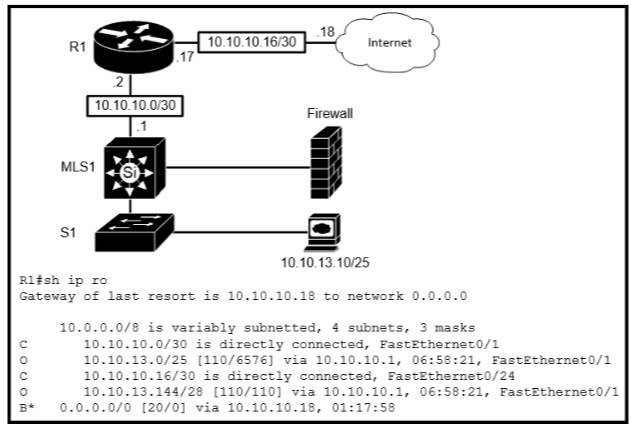
Which type of route does R1 use to reach host 10.10.13.10/32?
A.
floating static route
B.
host route
C.
default route
D.
network route
network route
Explanation: From the output, we see R1 will use the entry “O 10.10.13.0/25 [110/4576]
via 10.10.10.1, …” to reach host 10.10.13.10. This is a network route.Note: “B* 0.0.0.0/0
…” is a default route.
Which output displays a JSON data representation?
A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option C
Explanation: JSON data is written as name/value pairs.A name/value pair consists of a
field name (in double quotes), followed by a colon, followed by a value:“name”:”Mark”JSON
can use arrays. Array values must be of type string, number, object, array, boolean or
null.For example:{“name”:”John”,“age”:30,“cars”:[ “Ford”, “BMW”, “Fiat” ]}JSON can have
empty object like “taskId”:{}
An email user has been lured into clicking a link in an email sent by their company's
security organization. The webpage that opens reports that it was safe but the link could
have contained malicious code. Which type of security program is in place?
A.
Physical access control
B.
Social engineering attack
C.
brute force attack
D.
user awareness
user awareness
Explanation: This is a training program which simulates an attack, not a real attack (as it
says “The webpage that opens reports that it was safe”) so we believed it should be called
a “user awareness” program.Therefore the best answer here should be “user awareness”.
This is the definition of“User awareness” from CCNA 200- 301 Offical Cert Guide
Book:“User awareness: All users should be made aware of the need for data confidentiality
to protect corporate information, as well as their own credentials and personal information.
They should also be made aware of potential threats, schemes to mislead, and proper
procedures to report security incidents. ” Note: Physical access control means
infrastructure locations, such as network closets and data centers, should remain securely
locked.
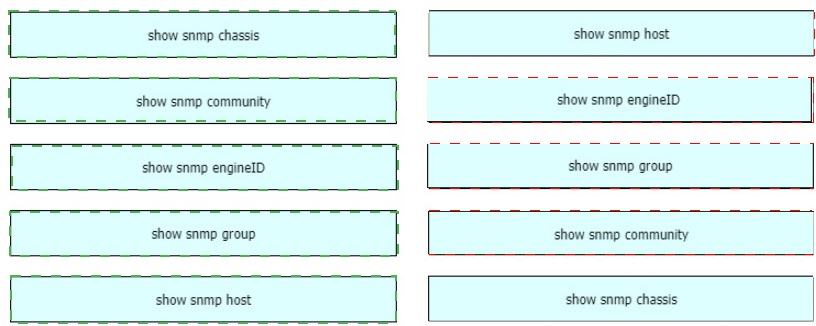
Drag and drop the SNMP manager and agent identifier commands from the left onto the
functions on the right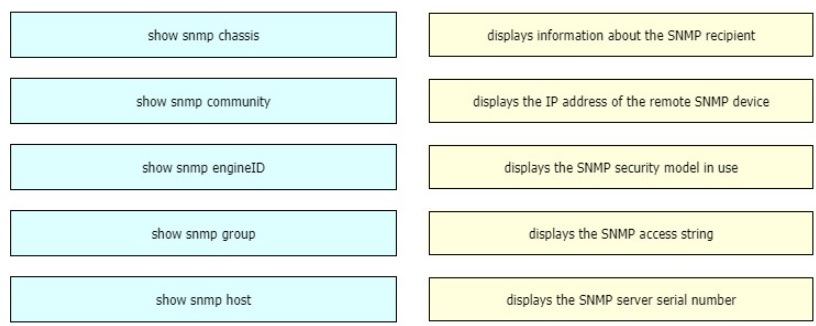
Which protocol does an IPv4 host use to obtain a dynamically assigned IP address?
A.
ARP
B.
DHCP
C.
CDP
D.
DNS
DHCP
| Page 4 out of 72 Pages |
| Previous |