Topic 2, Exam B
What are two differences between optical-fiber cabling and copper cabling? (Choose two)
A.
Light is transmitted through the core of the fiber
B.
A BNC connector is used for fiber connections
C.
The glass core component is encased in a cladding
D.
Fiber connects to physical interfaces using Rj-45 connections
E.
The data can pass through the cladding
Light is transmitted through the core of the fiber
The glass core component is encased in a cladding
An engineer needs to configure LLDP to send the port description time length value (TLV). What command sequence must be implemented?
A.
switch(config-line)#IIdp port-description
B.
switch(config)#IIdp port-description
C.
switch(config-if)#IIdp port-description
D.
switch#IIdp port-description
switch(config)#IIdp port-description
Which mode must be set for APs to communicate to a Wireless LAN Controller using the Control and Provisioning of Wireless Access Points (CAPWAP) protocol?
A.
bridge
B.
route
C.
autonomous
D.
lightweight
lightweight
When a client and server are not on the same physical network, which device is used to forward requests and replies between client and server for DHCP?
A.
DHCP relay agent
B.
DHCP server
C.
DHCPDISCOVER
D.
DHCPOFFER
DHCP relay agent
Which two primary drivers support the need for network automation? (Choose two.)
A.
Eliminating training needs
B.
Increasing reliance on self-diagnostic and self-healing
C.
Policy-derived provisioning of resources
D.
Providing a ship entry point for resource provisioning
E.
Reducing hardware footprint
Policy-derived provisioning of resources
Providing a ship entry point for resource provisioning
An administrator must secure the WLC from receiving spoofed association requests. Which
steps must be taken to configure the WLC to restrict the requests and force the user to wait
10 ms to retry an association request?
A.
Enable Security Association Teardown Protection and set the SA Query timeout to 10
B.
Enable MAC filtering and set the SA Query timeout to 10
C.
Enable 802.1x Layer 2 security and set me Comeback timer to 10
D.
Enable the Protected Management Frame service and set the Comeback timer to 10
Enable 802.1x Layer 2 security and set me Comeback timer to 10
What makes Cisco DNA Center different from traditional network management applications and their management of networks?
A.
It omits supports auto-discovery of network elements in a greenfield deployment.
B.
It modular design allows someone to implement different versions to meet the specific needs of an organization
C.
It abstracts policy from the actual device configuration
D.
It does not support high availability of management functions when operating in cluster
mode
It abstracts policy from the actual device configuration
Drag and drop the AAA terms from the left onto the description on the right.

Using direct sequence spread spectrum, which three 2.4-GHz channels are used to limit collisions?
A.
1,6,11
B.
1,5,10
C.
1,2,3
D.
5,6,7
1,6,11
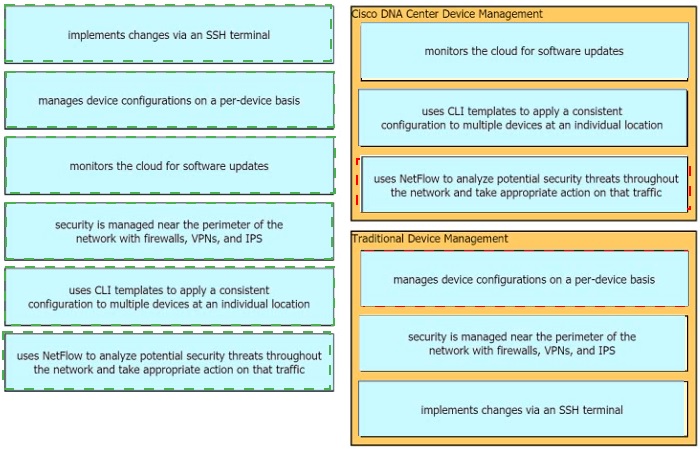
Drag the descriptions of device management from the left onto the types of device
management on the right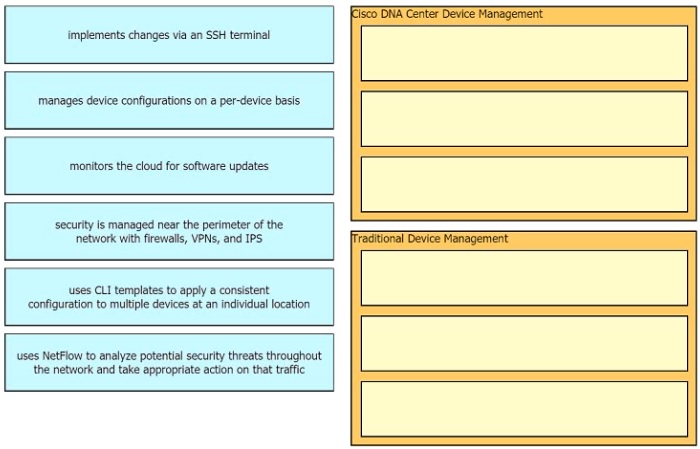
What are two benefits of using the PortFast feature? (Choose two )
A.
Enabled interfaces are automatically placed in listening state
B.
Enabled interfaces come up and move to the forwarding state immediately
C.
Enabled interfaces never generate topology change notifications.
D.
Enabled interfaces that move to the learning state generate switch topology change notifications
E.
Enabled interfaces wait 50 seconds before they move to the forwarding state
Enabled interfaces are automatically placed in listening state
Enabled interfaces come up and move to the forwarding state immediately
Refer to the exhibit.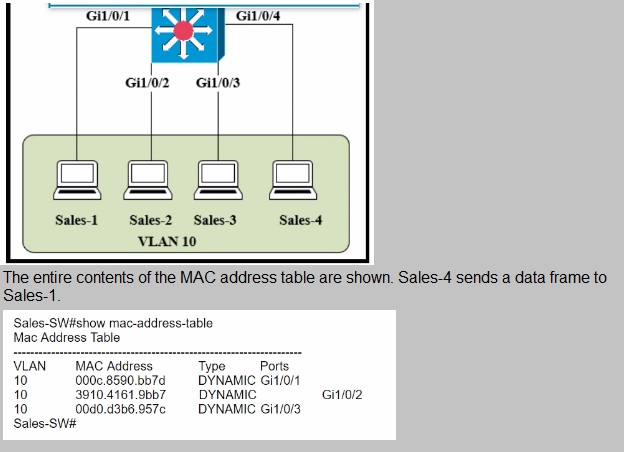
What does the switch do as it receives the frame from Sales-4?
A.
Perform a lookup in the MAC address table and discard the frame due to a missing entry.
B.
Insert the source MAC address and port into the forwarding table and forward the frame to Sales-1.
C.
Map the Layer 2 MAC address to the Layer 3 IP address and forward the frame.
D.
Flood the frame out of all ports except on the port where Sales-1 is connected.
Insert the source MAC address and port into the forwarding table and forward the frame to Sales-1.
Explanation: https://www.ciscopress.com/articles/article.asp?p=3089352&seqNum=6
| Page 34 out of 72 Pages |
| Previous |