Topic 2, Exam B
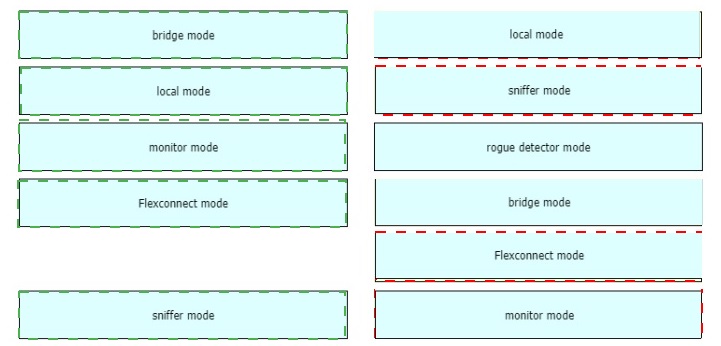
Drag and drop the lightweight access point operation modes from the left onto the
descriptions on the right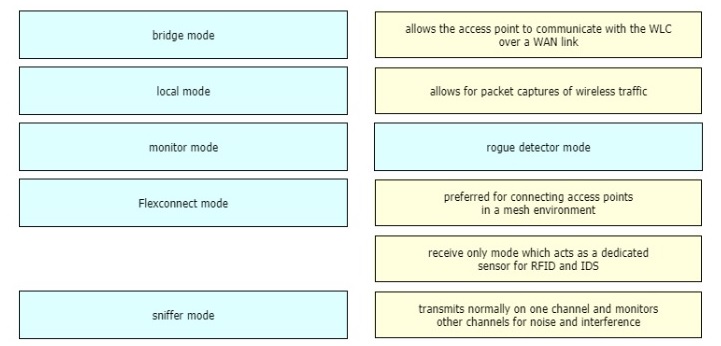
Which configuration management mechanism uses TCP port 22 by default when
communicating with managed nodes?
A.
Ansible
B.
Python
C.
Puppet
D.
Chef
Ansible
Refer to the exhibit

Which route does R1 select for traffic that is destined to 192 168.16.2?
A.
192.168.16.0/21
B.
192.168.16.0/24
C.
192.168 26.0/26
D.
192.168.16.0/27
192.168.16.0/27
Explanation: The destination IP addresses match all four entries in the routing table but
the 192.168.16.0/27 has the longest prefix so it will be chosen. This is called the “longest
prefix match” rule.
What are two descriptions of three-tier network topologies? (Choose two)
A.
The core and distribution layers perform the same functions
B.
The access layer manages routing between devices in different domains
C.
The network core is designed to maintain continuous connectivity when devices fail.
D.
The core layer maintains wired connections for each host
E.
The distribution layer runs Layer 2 and Layer 3 technologies
The network core is designed to maintain continuous connectivity when devices fail.
The distribution layer runs Layer 2 and Layer 3 technologies
Refer to the exhibit
How does router R1 handle traffic to 192.168.10.16?
A.
It selects the IS-IS route because it has the shortest prefix inclusive of the destination address.
B.
It selects the EIGRP route because it has the lowest administrative distance.
C.
It selects the OSPF route because it has the lowest cost.
D.
It selects the RIP route because it has the longest prefix inclusive of the destination
address.
It selects the RIP route because it has the longest prefix inclusive of the destination
address.
Which two actions influence the EIGRP route selection process? (Choose two)
A.
The router calculates the reported distance by multiplying the delay on the exiting
Interface by 256.
B.
The router calculates the best backup path to the destination route and assigns it as the
feasible successor.
C.
The router calculates the feasible distance of all paths to the destination route
D.
The advertised distance is calculated by a downstream neighbor to inform the local
router of the bandwidth on the link
E.
The router must use the advertised distance as the metric for any given route
The router calculates the best backup path to the destination route and assigns it as the
feasible successor.
The router calculates the feasible distance of all paths to the destination route
Explanation: The reported distance (or advertised distance) is the cost from the neighbor
to the destination. It is calculated from the router advertising the route to the network. For
example in the topology below, suppose router A & B are exchanging their routing tables
for the first time. Router B says “Hey, the best metric (cost) from me to IOWA is 50 and the
metric from you to IOWA is 90” and advertises it to router A.
Router A considers the first metric (50) as the Advertised distance. The second metric (90),
which is from NEVADA to IOWA (through IDAHO), is called the Feasible distance
Refer to the exhibit.
Which two prefixes are included in this routing table entry? (Choose two.)
A.
192.168.1.17
B.
192.168.1.61
C.
192.168.1.64
D.
192.168.1.127
E.
192.168.1.254
192.168.1.61
192.168.1.64
Refer to the exhibit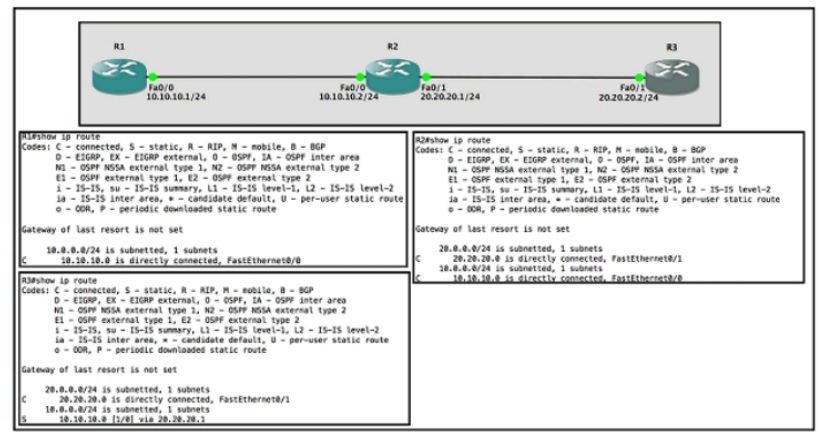
Router R1 Fa0/0 is unable ping router R3 Fa0/1.
Which action must be taken in router R1 to help resolve the configuration issue?
A.
set the default network as 20.20.20.0/24
B.
set the default gateway as 20.20.20.2
C.
configure a static route with Fa0/1 as the egress interface to reach the 20.20.20.0/24
network
D.
configure a static route with 10.10.10.2 as the next hop to reach the 20.20.20.0/24
network
configure a static route with 10.10.10.2 as the next hop to reach the 20.20.20.0/24
network
Refer to the exhibit.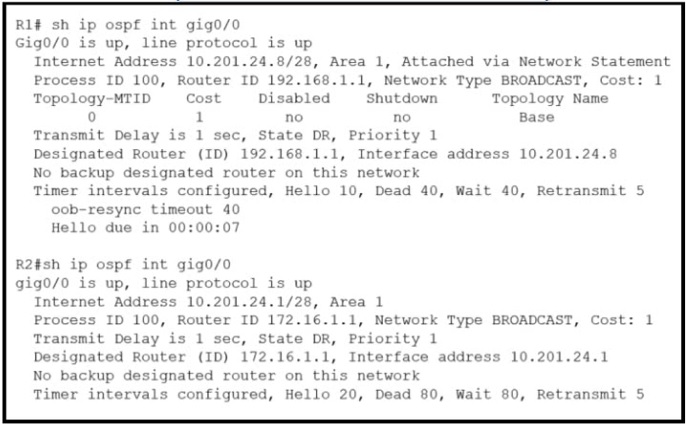
What action establishes the OSPF neighbor relationship without forming an adjacency?
A.
modify hello interval
B.
modify process ID
C.
modify priority
D.
modify network type
modify hello interval
Which protocol requires authentication to transfer a backup configuration file from a router to a remote server?
A.
DTP
B.
FTP
C.
SMTP
D.
TFTP
FTP
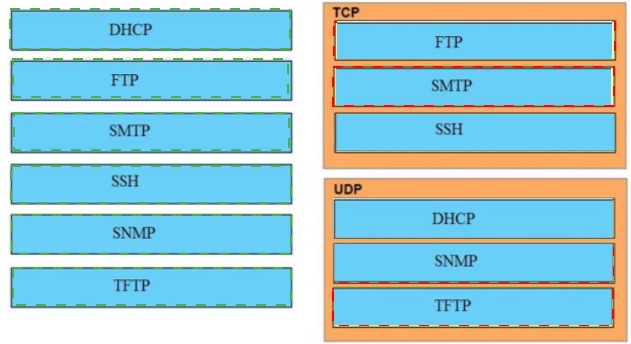
Drag and drop the application protocols from the left onto the transport protocols that it uses on the right
An engineer configured an OSPF neighbor as a designated router. Which state verifies the designated router is in the proper mode?
A.
Exchange
B.
2-way
C.
Full
D.
Init
Full
| Page 33 out of 72 Pages |
| Previous |