Topic 2, Exam B
Which port type supports the spanning-tree portfast command without additional
configuration?
A.
access ports
B.
Layer 3 main Interfaces
C.
Layer 3 suninterfaces
D.
trunk ports
access ports
Refer to the exhibit.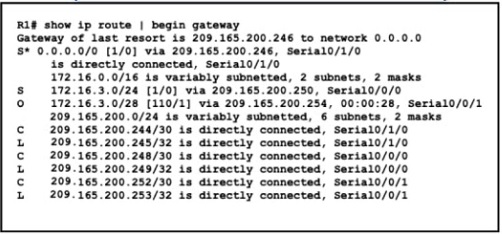
A packet is being sent across router R1 to host 172.16.0.14. What is the destination route
for the packet?
A.
209.165.200.254 via Serial0/0/1
B.
209.165.200.254 via Serial0/0/0
C.
209.165.200.246 via Serial0/1/0
D.
209.165.200.250 via Serial0/0/0
209.165.200.254 via Serial0/0/1
A network administrator needs to aggregate 4 ports into a single logical link which must negotiate layer 2 connectivity to ports on another switch What must be configured when using active mode on both sides of the connection?
A.
802.1q trunks
B.
Cisco vPC
C.
LLDP
D.
LACP
LACP
Refer to the exhibit.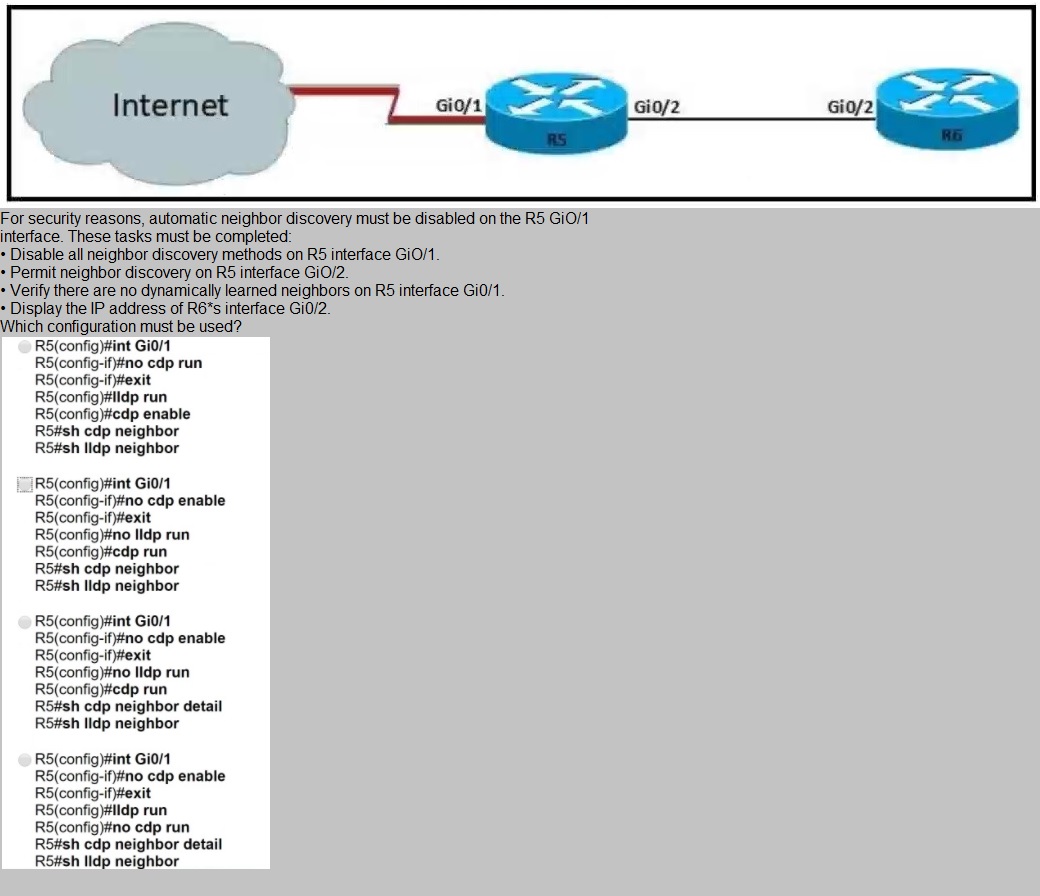
A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option C
When a WLAN with WPA2 PSK is configured in the Wireless LAN Controller GUI which format is supported?
A.
Unicode
B.
base64
C.
decimal
D.
ASCII
ASCII
Which set of action satisfy the requirement for multifactor authentication?
A.
The user swipes a key fob, then clicks through an email link
B.
The user enters a user name and password, and then clicks a notification in an
authentication app on a mobile device
C.
The user enters a PIN into an RSA token, and then enters the displayed RSA key on a
login screen
D.
The user enters a user name and password and then re-enters the credentials on a
second screen
The user enters a user name and password, and then clicks a notification in an
authentication app on a mobile device
Explanation: This is an example of how two-factor authentication (2FA) works:1. The user
logs in to the website or service with their username and password.2. The password is
validated by an authentication server and, if correct, the user becomes eligible for the
second factor.3. The authentication server sends a unique code to the user’s second-factor
method (such as a smartphone app).4. The user confirms their identity by providing the
additional authentication for their second-factor method.
A user configured OSPF in a single area between two routers A serial interface connecting
R1 and R2 is running encapsulation PPP By default which OSPF network type is seen on
this interface when the user types show ip ospf interface on R1 or R2?
A.
port-to-multipoint
B.
broadcast
C.
point-to-point
D.
nonbroadcast
point-to-point
Explanation: The default OSPF network type for HDLC and PPP on Serial link is point-topoint
(while the default OSPF network type for Ethernet link is Broadcast).
Refer to the exhibit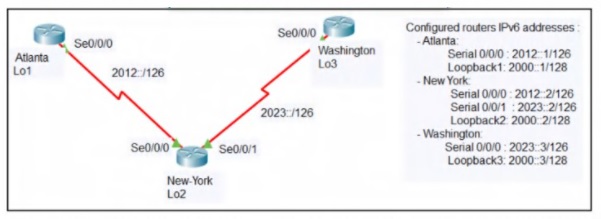
An engineer configured the New York router with state routes that point to the Atlanta and
Washington sites. When command must be configured on the Atlanta and Washington
routers so that both sites are able to reach the loopback2 interface on the New York
router?
A.
ipv6 route ::/0 Serial 0/0/1
B.
ipv6 route 0/0 Serial 0/0/0
C.
ipv6 route ::/0 Serial 0/0/0
D.
ip route 0.0.0.0.0.0.0.0 Serial 0/0/0
E.
ipv6 route ::/0 2000::2
ipv6 route ::/0 Serial 0/0/0
What benefit does controller-based networking provide versus traditional networking?
A.
moves from a two-tier to a three-tier network architecture to provide maximum
redundancy
B.
provides an added layer of security to protect from DDoS attacks
C.
allows configuration and monitoring of the network from one centralized port
D.
combines control and data plane functionality on a single device to minimize latency
allows configuration and monitoring of the network from one centralized port
Which type of traffic Is sent with pure iPsec?
A.
broadcast packets from a switch that is attempting to locate a MAC address at one of several remote sites
B.
multicast traffic from a server at one site to hosts at another location
C.
spanning-tree updates between switches that are at two different sites
D.
unicast messages from a host at a remote site lo a server at headquarters
unicast messages from a host at a remote site lo a server at headquarters
Explanation: “The original poster makes a correct observation that EIGRP does not work
in a pure IPSEC environment. IPSEC was designed to process unicast traffic.
Which communication interaction takes place when a southbound API Is used?
A.
between the SDN controller and PCs on the network
B.
between the SON controller and switches and routers on the network
C.
between the SON controller and services and applications on the network
D.
between network applications and switches and routers on the network
between the SON controller and switches and routers on the network
Refer to the exhibit.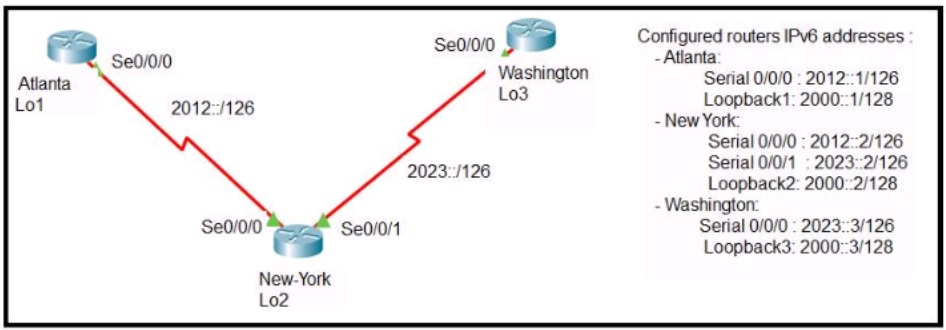
The New York router is configured with static routes pointing to the Atlanta and Washington
sites. Which two tasks must be performed so that the Serial0/0/0 interfaces on the Atlanta
and Washington routers can reach one another?
(Choose two.)
A.
Configure the ipv6 route 2012::/126 2023::1 command on the Washington router.
B.
Configure the ipv6 route 2023::/126 2012::1 command on the Atlanta router.
C.
Configure the Ipv6 route 2012::/126 s0/0/0 command on the Atlanta router.
D.
Configure the ipv6 route 2023::/126 2012::2 command on the Atlanta router.
E.
Configure the ipv6 route 2012::/126 2023::2 command on the Washington router.
Configure the ipv6 route 2023::/126 2012::2 command on the Atlanta router.
Configure the ipv6 route 2012::/126 2023::2 command on the Washington router.
Explanation: The short syntax of static IPv6 route is:ipv6 route <destination-IPv6-address>
{next-hop-IPv6-address | exit-interface}
| Page 27 out of 72 Pages |
| Previous |