Topic 2, Exam B
Refer to the exhibit.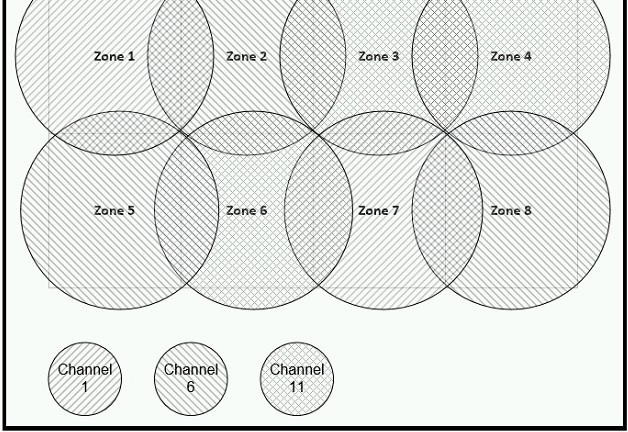
Between which zones do wireless users expect to experience intermittent connectivity?
A.
between zones 1 and 2
B.
between zones 2 and 5
C.
between zones 3 and 4
D.
between zones 3 and 6
between zones 3 and 6
Refer to the exhibit.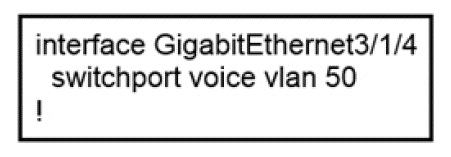
An administrator is tasked with configuring a voice VLAN. What is the expected outcome when a Cisco phone is connected to the GigabitEfriemet3/1/4 port on a switch?
A.
The phone and a workstation that is connected to the phone do not have VLAN connectivity
B.
The phone and a workstation that is connected to the phone send and receive data in VLAN 50.
C.
The phone sends and receives data in VLAN 50, but a workstation connected to the phone has no VLAN connectivity
D.
The phone sends and receives data in VLAN 50, but a workstation connected to the phone sends and receives data in VLAN 1
The phone sends and receives data in VLAN 50, but a workstation connected to the phone sends and receives data in VLAN 1
Refer to the exhibit
A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option B
Explanation: ipv6 unicast-routing statement included (IPv6 is enabled on the
router).Compared to the exhibit, Fa0/0 and Fa0/1 have correct configurations.The route to
subnet 2001:db8:4::/64 points to R18’s Fa1/0 (correct next-hop).
Refer to the exhibit.
If R1 receives a packet destined to 172.161.1, to which IP address does it send the packet?
A.
192.168.12.2
B.
192.168.13.3
C.
192.168.14.4
D.
192.168.15.5
192.168.14.4
Refer to the exhibit.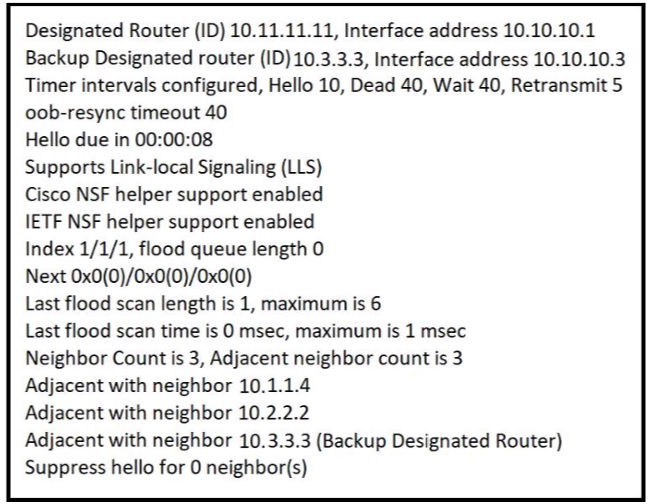
The show ip ospf interface command has been executed on R1 How is OSPF configured?
A.
The interface is not participating in OSPF
B.
A point-to-point network type is configured
C.
The default Hello and Dead timers are in use
D.
There are six OSPF neighbors on this interface
The default Hello and Dead timers are in use
Explanation: https://www.cisco.com/c/en/us/support/docs/ip/open-shortest-path-firstospf/
13689-17.html
Refer to the exhibit.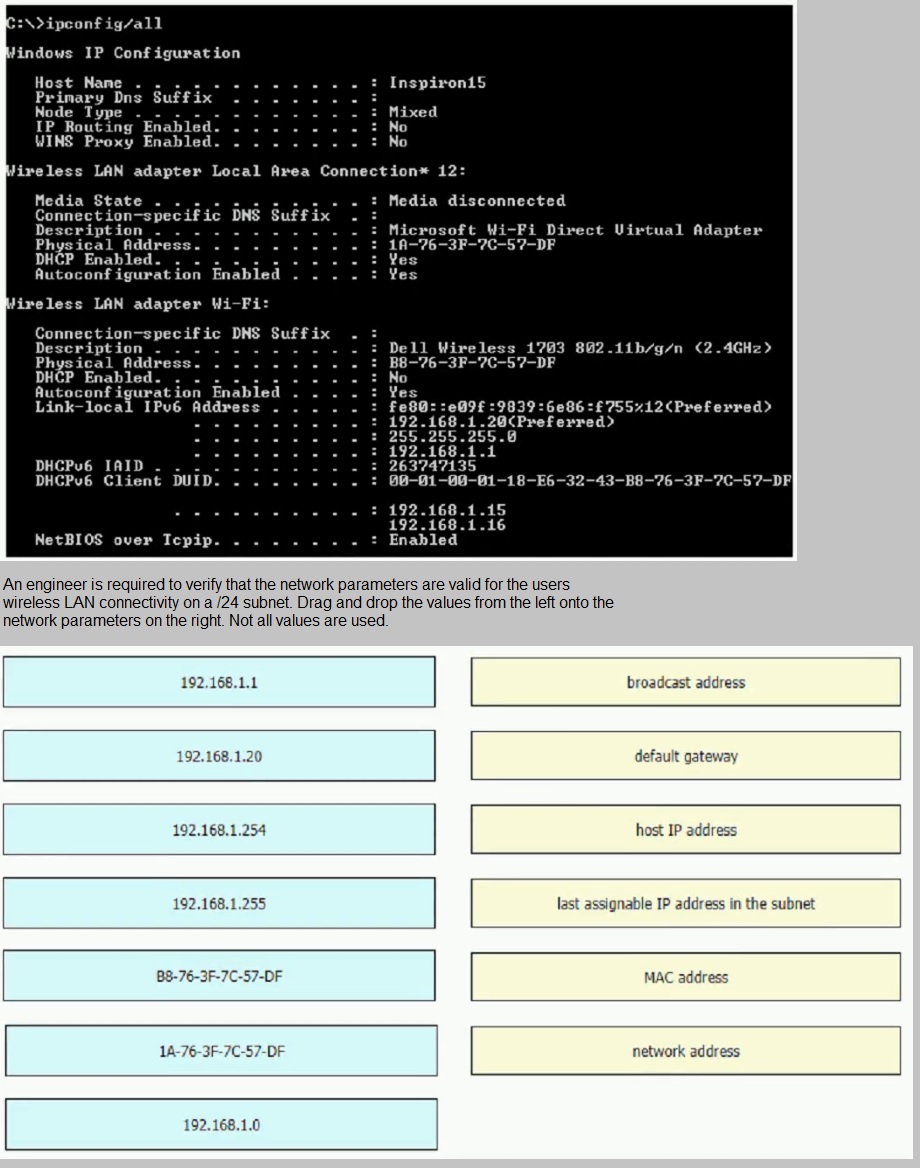
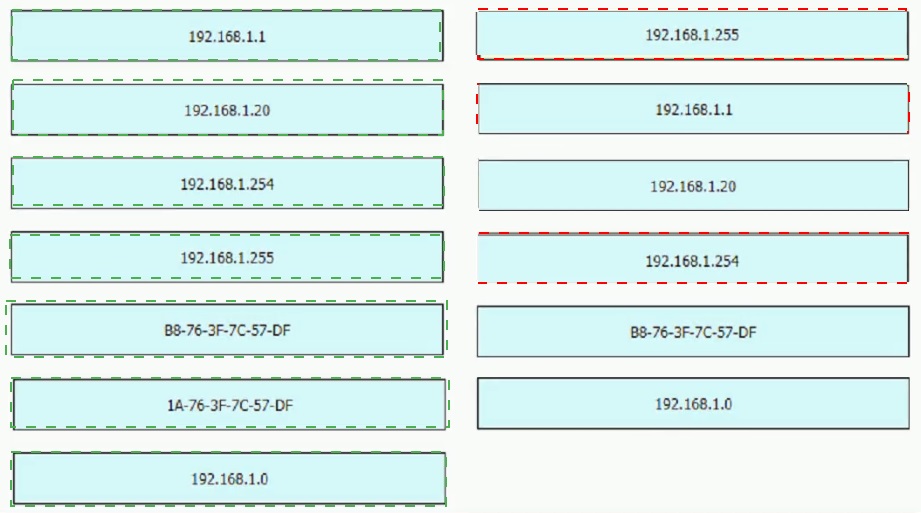
What are two characteristics of an SSID? (Choose Two)
A.
It can be hidden or broadcast in a WLAN
B.
It uniquely identifies an access point in a WLAN
C.
It uniquely identifies a client in a WLAN
D.
It is at most 32 characters long.
E.
IT provides secured access to a WLAN
It uniquely identifies an access point in a WLAN
IT provides secured access to a WLAN
Which command must be entered when a device is configured as an NTP server?
A.
ntp authenticate
B.
ntp server
C.
ntp peer
D.
ntp master
ntp master
Explanation: To configure a Cisco device as an Authoritative NTP Server, use the ntp master [stratum] command.To configure a Cisco device as a NTP client, use the command ntp server <IP address>. For example:Router(config)#ntp server 192.168.1.1. This
command will instruct the router to query 192.168.1.1 for the time.
An engineer requires a scratch interface to actively attempt to establish a trunk link with a neighbor switch. What command must be configured?
A.
switchport mode trunk
B.
switchport mode dynamic desirable
C.
switchport mode dynamic auto
D.
switchport nonegotiate
switchport mode dynamic auto
Which action does the router take as rt forwards a packet through the network?
A.
The router replaces the source and desinaoon labels wth the sending router uterface
label as a source and the next hop router label as a desbnabon
B.
The router encapsulates the source and destination IP addresses with the sending
router P address as the source and the neighbor IP address as the destination
C.
The router replaces the original source and destination MAC addresses with the sending
router MAC address as the source and neighbor MAC address as the destination
D.
The router encapsulates the original packet and then includes a tag that identifies the
source router MAC address and transmit transparently to the destination
The router replaces the original source and destination MAC addresses with the sending
router MAC address as the source and neighbor MAC address as the destination
How do AAA operations compare regarding user identification, user services and access control?
A.
Authorization provides access control and authentication tracks user services
B.
Authentication identifies users and accounting tracks user services
C.
Accounting tracks user services, and authentication provides access control
D.
Authorization identifies users and authentication provides access control
Authentication identifies users and accounting tracks user services
What Is the path for traffic sent from one user workstation to another workstation on a separate switch In a Ihree-lter architecture model?
A.
access - core - distribution - access
B.
access - distribution - distribution - access
C.
access - core - access
D.
access -distribution - core - distribution - access
access -distribution - core - distribution - access
| Page 22 out of 72 Pages |
| Previous |