Topic 1: Exam Pool A
desc about topic
Which command automatically generates an IPv6 address from a specified IPv6 prefix and MAC address of an interface?
A.
ipv6 address dhcp
B.
ipv6 address 2001:DB8:5:112::/64 eui-64
C.
ipv6 address autoconfig
D.
ipv6 address 2001:DB8:5:112::2/64 link-local
ipv6 address autoconfig
Explanation: The “ipv6 address autoconfig” command causes the device to perform IPv6
stateless address autoconfiguration to discover prefixes on the link and then to add the
Refer to the exhibit.
A router reserved these five routes from different routing information sources.
Which two routes does the router install in its routing table? (Choose two)
A.
RIP route 10.0.0.0/30
B.
iBGP route 10.0.0.0/30
C.
OSPF route 10.0.0.0/30
D.
EIGRP route 10.0.0.1/32
E.
OSPF route 10.0.0.0/16
OSPF route 10.0.0.0/30
EIGRP route 10.0.0.1/32
What protocol allows an engineer to back up 20 network router configurations globally while using the copy function?
A.
SMTP
B.
SNMP
C.
TCP
D.
FTP
SNMP
An engineer must configure Interswitch VLAN communication between a Cisco switch and a third-party switch. Which action should be taken?
A.
configure IEEE 802.1p
B.
configure IEEE 802.1q
C.
configure ISL
D.
configure DSCP
configure IEEE 802.1q
Which implementation provides the strongest encryption combination for the wireless environment?
A.
WPA2 + AES
B.
WPA + AES
C.
WEP
D.
WPA + TKIP
WPA2 + AES
Which two encoding methods are supported by REST APIs? (Choose two)
A.
YAML
B.
JSON
C.
EBCDIC
D.
SGML
E.
XML
JSON
XML
Explanation: https://www.cisco.com/c/en/us/td/docs/switches/datacenter/aci/apic/sw/2-
x/rest_cfg/2_1_x/b_Cisco_APIC_REST_API_Configuration_Guide/b_Cisco_APIC_REST_
API_Configuration_Guide_chapter_01.html
Reference:
https://www.cisco.com/c/en/us/td/docs/switches/datacenter/nexus1000/sw/5_x/rest_api_co
nfig/b_Cisco_N1KV_VMware_REST_API_Config_5x/b_Cisco_N1KV_VMware_REST_API
_Config_5x_chapter_010.pdf
The Application Policy Infrastructure Controller (APIC) REST API is a programmatic
interface that uses REST architecture. The API accepts and returns HTTP (not enabled by
default) or HTTPS messages that contain JavaScript Object Notation (JSON) or Extensible
Markup Language (XML) documents.
What is the primary purpose of a First Hop Redundancy Protocol?
A.
It allows directly connected neighbors to share configuration information.
B.
It allows a router to use bridge priorities to create multiple loop-free paths to a single destination.
C.
It reduces routing failures by allowing Layer 3 load balancing between OSPF neighbors that have the same link metric.
D.
It reduces routing failures by allowing more than one router to represent itself, as the
default gateway of a network.
It reduces routing failures by allowing more than one router to represent itself, as the
default gateway of a network.
What is the primary effect of the spanning-tree portfast command?
A.
it enables BPDU messages
B.
It minimizes spanning-tree convergence time
C.
It immediately puts the port into the forwarding state when the switch is reloaded
D.
It immediately enables the port in the listening state
It minimizes spanning-tree convergence time
Reference:
https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3560/software/release/12-
2_55_se/configuration/guide/3560_scg/swstpopt.html
Refer to the exhibit.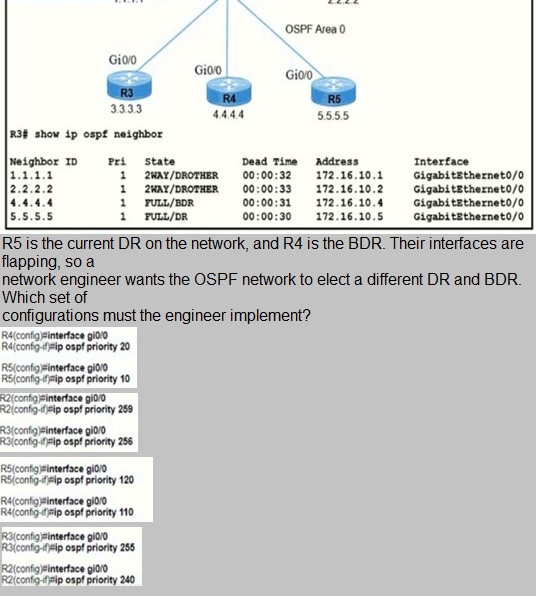
A.
Option
B.
Option
C.
Option
D.
Option
Option
When a site-to-site VPN is configured, which IPsec mode provides encapsulation and encryption of the entire original P packet?
A.
IPsec tunnel mode with AH
B.
IPsec transport mode with AH
C.
IPsec tunnel mode with ESP
D.
IPsec transport mode with ESP
IPsec tunnel mode with ESP
Explanation: “Encapsulating Security Payload…Unlike Authentication Header (AH), ESP
in transport mode does not provide integrity and authentication for the entire IP packet.
However, in Tunnel Mode, where the entire original IP packet is encapsulated with a new
packet header added, ESP protection is afforded to the whole inner IP packet (including the
inner header) while the outer header (including any outer IPv4 options or IPv6 extension
headers) remains unprotected.
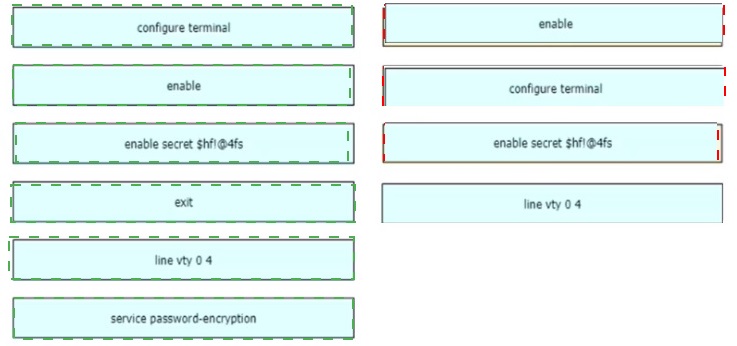
An engineer is configuring an encrypted password for the enable command on a router
where the local user database has already been configured Drag and drop the
configuration commands from the left into the correct sequence on the right Not all
commands are used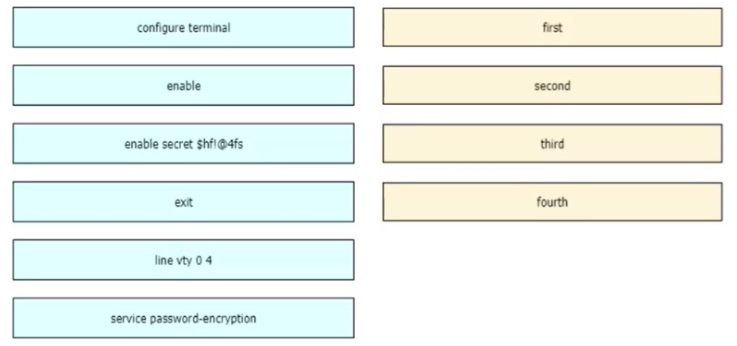
Which statement identifies the functionality of virtual machines?
A.
Virtualized servers run most efficiently when they are physically connected to a switch that is separate from the hypervisor
B.
The hypervisor can virtualize physical components including CPU. memory, and storage
C.
Each hypervisor can support a single virtual machine and a single software switch
D.
The hypervisor communicates on Layer 3 without the need for additional resources
The hypervisor can virtualize physical components including CPU. memory, and storage
| Page 18 out of 72 Pages |
| Previous |