Topic 1: Exam Pool A
desc about topic
Refer to Exhibit.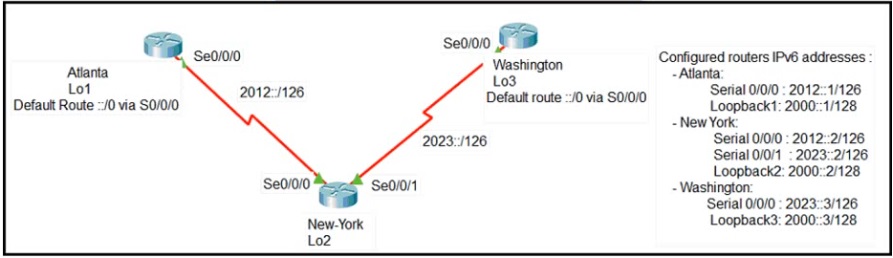
The loopback1 interface of the Atlanta router must reach the loopback3 interface of the
Washington router. Which two static host routes must be configured on the NEW York
router? (Choose two)
A.
ipv6 route 2000::1/128 2012::1
B.
ipv6 route 2000::3/128 2023::3
C.
ipv6 route 2000::3/128 s0/0/0
D.
ipv6 route 2000::1/128 2012::2
E.
ipv6 route 2000::1/128 s0/0/1
ipv6 route 2000::1/128 2012::1
ipv6 route 2000::3/128 2023::3
Which function does the range of private IPv4 addresses perform?
A.
allows multiple companies to each use the same addresses without conflicts
B.
provides a direct connection for hosts from outside of the enterprise network
C.
ensures that NAT is not required to reach the internet with private range addressing
D.
enables secure communications to the internet for all external hosts
allows multiple companies to each use the same addresses without conflicts
What is the purpose of traffic shaping?
A.
to mitigate delays over slow links
B.
to provide fair queuing for buffered flows
C.
to limit the bandwidth that a flow can use to
D.
be a marking mechanism that identifies different flows
to provide fair queuing for buffered flows
Explanation: Traffic shaping retains excess packets in a queue and then schedules the
excess for later transmission over increments of time.
What is the role of a firewall in an enterprise network?
A.
Forwards packets based on stateless packet inspection
B.
Processes unauthorized packets and allows passage to less secure segments of the network
C.
determines which packets are allowed to cross from unsecured to secured networks
D.
explicitly denies all packets from entering an administrative domain
determines which packets are allowed to cross from unsecured to secured networks
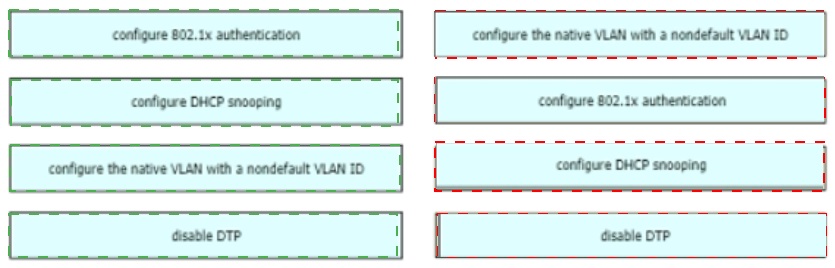
Drag and drop the attack-mitigation techniques from the left onto the Types of attack that they mitigate on the right.
Which 802.11 frame type is association response?
A.
management
B.
protected frame
C.
control
D.
action
management
Reference: https://en.wikipedia.org/wiki/802.11_Frame_Types
What is a function of Wireless LAN Controller?
A.
register with a single access point that controls traffic between wired and wireless endpoints.
B.
use SSIDs to distinguish between wireless clients.
C.
send LWAPP packets to access points.
D.
monitor activity on wireless and wired LANs
send LWAPP packets to access points.
Explanation: Lightweight APs (LAPs) is devices require no initial configuration. LAPs use the Lightweight Access Point Protocol (LWAPP) to communicate with a WLAN controller (WLC), as shown in the below figure. Controller-based APs are useful in situations where many APs are required in the network. As more APs are added, each AP is automatically configured and managed by the WLC.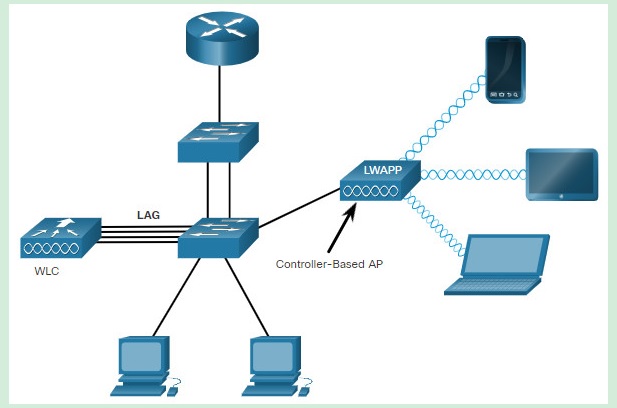
What is the benefit of using FHRP?
A.
reduced management overhead on network routers
B.
balancing traffic across multiple gateways in proportion to their loads
C.
higher degree of availability
D.
reduced ARP traffic on the network
higher degree of availability
Which option about JSON is true?
A.
uses predefined tags or angle brackets () to delimit markup text
B.
used to describe structured data that includes arrays
C.
used for storing information
D.
similar to HTML, it is more verbose than XML
used to describe structured data that includes arrays
Explanation: JSON data is written as name/value pairs.A name/value pair consists of a
field name (in double quotes), followed by a colon, followed by a value:“name”:”Mark”JSON
can use arrays. Array values must be of type string, number, object, array, boolean or
null..For example:{“name”:”John”,“age”:30,“cars”:[ “Ford”, “BMW”, “Fiat” ]}
How does Cisco DNA Center gather data from the network?
A.
Network devices use different services like SNMP, syslog, and streaming telemetry to send data to the controller
B.
Devices establish an iPsec tunnel to exchange data with the controller
C.
Devices use the call-home protocol to periodically send data to the controller.
D.
The Cisco CU Analyzer tool gathers data from each licensed network device and streams it to the controller.
Network devices use different services like SNMP, syslog, and streaming telemetry to send data to the controller
which purpose does a northbound API serve in a controller-based networking architecture?
A.
communicates between the controller and the physical network hardware
B.
reports device errors to a controller
C.
generates statistics for network hardware and traffic
D.
facilitates communication between the controller and the applications
facilitates communication between the controller and the applications
A network administrator is asked to configure VLANS 2, 3 and 4 for a new implementation. Some ports must be assigned to the new VLANS with unused remaining. Which action should be taken for the unused ports?
A.
configure port in the native VLAN
B.
configure ports in a black hole VLAN
C.
configure in a nondefault native VLAN
D.
configure ports as access ports
configure ports in a black hole VLAN
| Page 14 out of 72 Pages |
| Previous |