Topic 1: Exam Pool A
desc about topic
What is recommended for the wireless infrastructure design of an organization?
A.
group access points together to increase throughput on a given channel
B.
configure the first three access points are configured to use Channels 1, 6, and 11
C.
include a least two access points on nonoverlapping channels to support load balancing
D.
assign physically adjacent access points to the same Wi-Fi channel
configure the first three access points are configured to use Channels 1, 6, and 11
When DHCP is configured on a router, which command must be entered so the default gateway is automatically distributed?
A.
default-router
B.
default-gateway
C.
ip helper-address
D.
dns-server
default-router
Which WLC port connects to a switch to pass normal access-point traffic?
A.
redundancy
B.
console
C.
distribution system
D.
service
distribution system
Which QoS Profile is selected in the GUI when configuring a voice over WLAN
deployment?
A.
Bronze
B.
Platinum
C.
Silver
D.
Gold
Platinum
Reference: https://www.cisco.com/c/en/us/support/docs/wireless-mobility/wireless-lanwlan/
81831-qos-wlc-lap.html
Cisco Unified Wireless Network solution WLANs support four levels of QoS:
Platinum/Voice, Gold/Video, Silver/Best Effort (default), and Bronze/Background.
After running the code in the exhibit, which step reduces the amount of data that the
NETCONF server returns to the NETCONF client, to only the interface's configuration?
A.
Use the Ixml library to parse the data returned by the NETCONF server for the
interface's configuration.
B.
Create an XML filter as a string and pass it to get_config() method as an argument.
C.
Create a JSON filter as a string and pass it to the get_config() method as an argument.
D.
Use the JSON library to parse the data returned by the NETCONF server for the
interface's configuration.
Use the JSON library to parse the data returned by the NETCONF server for the
interface's configuration.
What criteria is used first during me root port selection process?
A.
local port ID
B.
lowest path cost to the root bridge
C.
lowest neighbor's bridge ID
D.
lowest neighbor's port ID
lowest path cost to the root bridge
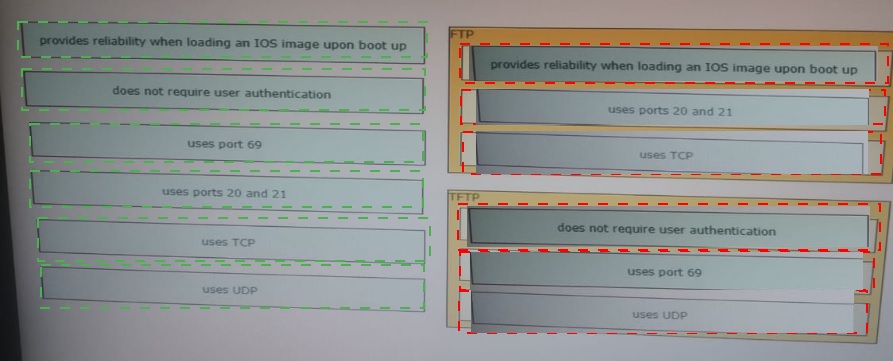
Drag and drop the descriptions of file-transfer protocols from the left onto the correct protocols on the right.
Refer to the exhibit.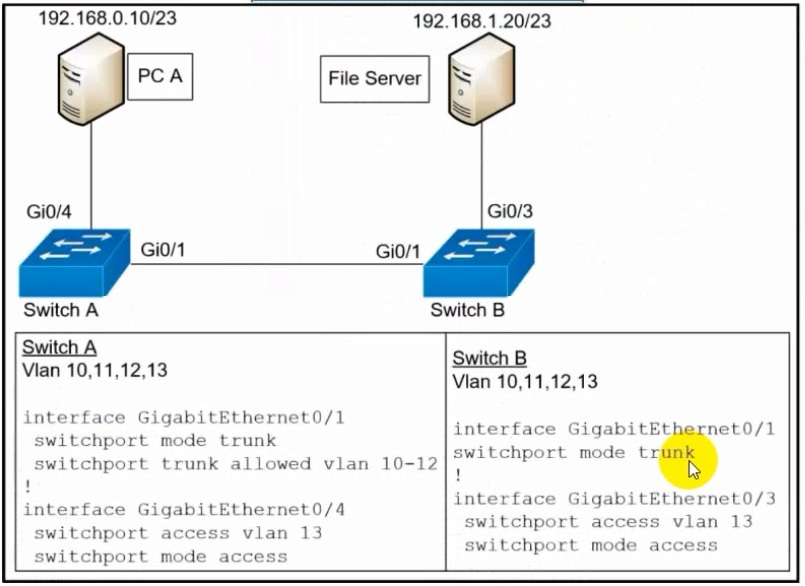
A network engineer must configured communication between PC A and the File Server. To
prevent interruption for any other communications, which command must be configured?
A.
Switch trunk allowed vlan 12
B.
Switchport trunk allowed vlan none
C.
Switchport trunk allowed vlan add 13
D.
Switchport trunk allowed vlan remove 10-11
Switchport trunk allowed vlan add 13
Refer to the exhibit.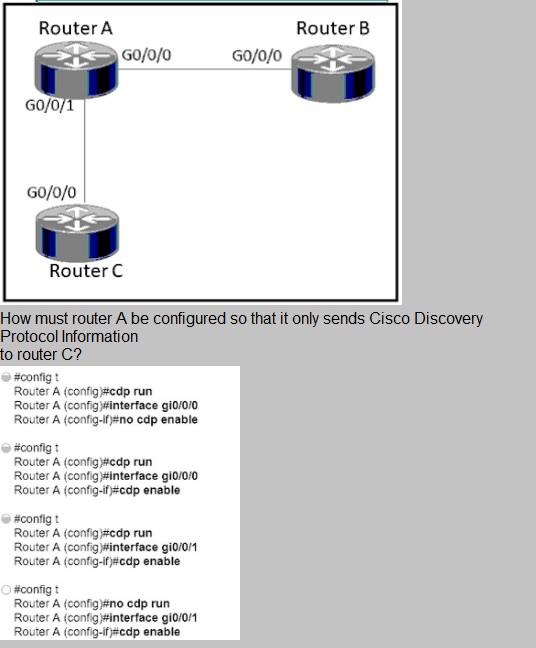
A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option D
Which type of security program is violated when a group of employees enters a building using the ID badge of only one person?
A.
intrusion detection
B.
user awareness
C.
physical access control
D.
network authorization
physical access control
Which security program element involves installing badge readers on data-center doors to allow workers to enter and exit based on their job roles?
A.
role-based access control
B.
biometrics
C.
multifactor authentication
D.
physical access control
physical access control
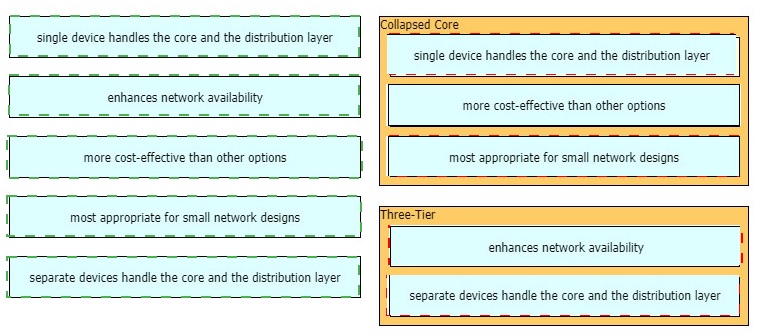
Drag and drop the characteristics of network architectures from the left onto the type of architecture on the right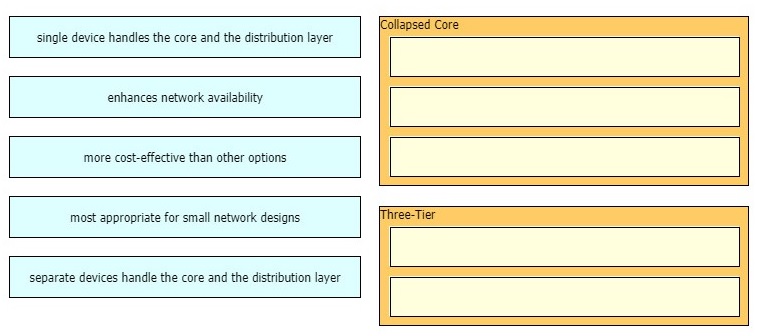
| Page 12 out of 72 Pages |
| Previous |