What is the difference between statistical detection and rule-based detection models?
A.
Rule-based detection involves the collection of data in relation to the behavior of legitimate users over a period of time
B.
Statistical detection defines legitimate data of users over a period of time and rule-based detection defines it on an IF/THEN basis
C.
Statistical detection involves the evaluation of an object on its intended actions before it executes that behavior
D.
Rule-based detection defines legitimate data of users over a period of time and
statistical detection defines it on an IF/THEN basis
Statistical detection defines legitimate data of users over a period of time and rule-based detection defines it on an IF/THEN basis
Refer to the exhibit. Which type of log is displayed?
Which type of log is displayed?
A.
AIDS
B.
proxy
C.
NetFlow
D.
sys
sys
Which principle is being followed when an analyst gathers information relevant to a security incident to determine the appropriate course of action?
A.
decision making
B.
rapid response
C.
data mining
D.
due diligence
decision making
Which NIST IR category stakeholder is responsible for coordinating incident response among various business units, minimizing damage, and reporting to regulatory agencies?
A.
CSIRT
B.
BPSIRT
C.
public affairs
D.
management
management
What causes events on a Windows system to show Event Code 4625 in the log
messages?
A.
The system detected an XSS attack
B.
Someone is trying a brute force attack on the network
C.
Another device is gaining root access to the system
D.
A privileged user successfully logged into the system
Someone is trying a brute force attack on the network
When trying to evade IDS/IPS devices, which mechanism allows the user to make the data incomprehensible
without a specific key, certificate, or password?
A.
fragmentation
B.
pivoting
C.
encryption
D.
stenography
pivoting
What is the difference between an attack vector and attack surface?
A.
An attack surface identifies vulnerabilities that require user input or validation; and anVattack vector
identifies vulnerabilities that are independent of user actions.
B.
An attack vector identifies components that can be exploited; and an attack surface
identifies the potential
path an attack can take to penetrate the network.
C.
An attack surface recognizes which network parts are vulnerable to an attack; and an
attack vector
identifies which attacks are possible with these vulnerabilities.
D.
An attack vector identifies the potential outcomes of an attack; and an attack surface
launches an attack
using several methods against the identified vulnerabilities.
An attack surface recognizes which network parts are vulnerable to an attack; and an
attack vector
identifies which attacks are possible with these vulnerabilities.
What is personally identifiable information that must be safeguarded from unauthorized access?
A.
date of birth
B.
driver's license number
C.
gender
D.
zip code
driver's license number
While viewing packet capture data, an analyst sees that one IP is sending and receivingVtraffic for multiple devices by modifying the IP header.
Which technology makes this behavior possible?
A.
encapsulation
C.
tunneling
D.
NAT
NAT
Drag and drop the security concept on the left onto the example of that concept on the right.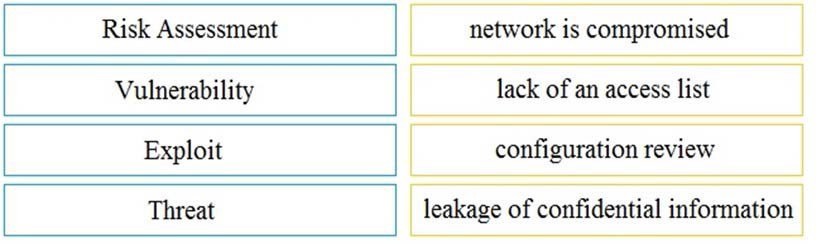
Refer to the exhibit.
What does the message indicate?
A.
an access attempt was made from the Mosaic web browser
B.
a successful access attempt was made to retrieve the password file
C.
a
D.
a denied access attempt was made to retrieve the password file
a
Which process is used when IPS events are removed to improve data integrity?
A.
data availability
B.
data normalization
C.
data signature
D.
data protection
data normalization
| Page 6 out of 16 Pages |
| Previous |